TheArbiter's Posts
Nairaland Forum / TheArbiter's Profile / TheArbiter's Posts
(1) (2) (3) (4) (5) (6) (7) (8) (of 8 pages)
If the Igbo ethnic people do leave the Nigerian Federation! It would be a vindication of the victory of mass hysteria, hypocrisy, hate, ignorance, Igbo inferiority complex, media hype and shallow intellect over lucid logic. It will be a first hand lesson for peeps in Nairaland regarding how pride, hate, poor leadership and mob ignorance (of ipob members) consigns whole innocent populations to misery and death akin to that of bokoharam in Northern Nigeria. It is no secret that this absence of logical thinking had always been the bane of the African mind and intellect. It had even been inferred that this might account for the few great leaders among Africans. Now to the question, how will the Igbo ethnic people leave the Nigerian Federation? It depends on how it occurs. If ipob follows the UN route it will take 5 to 10 years to realize the Igbo nation and the process will follow a series of structured stages as was done in the Sudan case. This will however, depend on how much opposition (country support) ipob can bring to bear against the Nigerian argument at UN committee hearings. For example, a UN referendum as demanded by ipob cannot hold within 2 years even if Nigeria agrees to it as their will be discussions on funding, supervision, legitimacy under Nigerian constitution, etc If the ipob were to follow the violent route, then it must be prepared to fight a longer and more brutal war than Ojukwu did (approximately 4 years plus). However, I do not think ipob has the balls for what Ojukwu did. For reference, Ojukwu was among the finest military officers of his time. He had the utmost respect for his military peers but was aware of the limitations of the Nigerian army then. He took a great gamble on this limitations, a shot at greatness which he envisioned, but the odds were not in his favor. He also knew the price of failure, it will be thrice more difficult to repeat the same gamble unless if the Nigerian state weakens considerable which I do not foresee. Furthermore, the Biafra currency cannot and will never have the value it had in 1967 for lucid reasons: In 1967, part of Nigeria's national gold reserve (how many people know we have a gold reserve?) was domiciled in the eastern regional central bank and hence partly accounted for the Biafra currency value. After that experience (civil war), it is now centrally domiciled in one place. Additionally, Ojukwu had seasoned technocrats running administration and finances compared to what is obtainable now. I do not foresee Okonjo Iweala and their likes rushing home to lead the economic teams in what may degenerate into a war zone. Ojukwu also had diplomatic and military presence, had military hardware, a substantially trained army and police to maintain order. Finally, Ojukwu offered alternative lucrative deals to IOC’s, after seizing the Niger delta areas, for support against Nigeria. Furthermore, it is obvious the Niger Deltans will not follow the Igbo action for obvious reasons: The Niger Deltans had not forgotten the servitude they faced under Igbo domination, during the civil war, regardless of what the current ipob propaganda says. Nay, rather they will rather quietly observe and encourage the ipob madness to their advantage, because: Ipob has not offered them anything better compared to the current existing situation under Nigeria. They see a resource and power hungry ipob compared to the current amenable Federal government, which had opened a listening ear to what they want. More federal allocation will be available for them to spend, more contracts, etc if ipob secedes All federal appointments occupied by the Igbos automatically devolve to them. They will take over all businesses and properties forfeited by the Igbos in their lands after they secede. The Igbos access to the sea becomes a source of revenue as they can impose a mafia like port access control, which may be more lucrative than the current prevalent crime of kidnapping. Finally, they will have the Igbos by the balls for the first time since the undocumented atrocities they committed against them during the civil war. If the Igbo ethnic people leave the Nigerian Federation today There will be an exodus of about 20 million people. Up to 18 million Igbo foreigners will move from other parts of Nigeria into Igbo land. Up to 2 million Nigerians will move from the five Igbo states to Nigerian soil. All Igbos will require visa to visit anywhere in Nigeria. The ipob propaganda machine targeted at dividing the west along religious fault lines in an effort to gain Christian support to stay in the western region rather than the north is obviously stupid. Note that even the ipob leader himself is not even a Christian. The exodus will affect over 9 million Igbo youths: students, pupils, employed and unemployed. This includes university and secondary school students outside of Igbo land. Most of the youths will be conscripted to farm, teach or join communist-like production outfits to sustain the about 40 million (estimated) people in the new Igbo nation. The exodus from Nigeria will include businessmen, former government employees, teachers, doctors, factory workers, gala sellers, etc. Igbo businesses and properties in Nigerian territory, regardless of ownership, may become forfeit against the existing debts by the Igbo states for which Nigeria stand surety Properties and businesses worth billions will be mortgaged to Nigerian banks by the Igbo foreigners or hidden under secondary ownership schemes to evade forfeiture. Property prices will drop in Nigeria as properties are sold at giveaway prices and large estates become empty. Housing, security, health and social problems will skyrocket in Igbo land due to poor or an absence of critical infrastructure. Nigeria will block and heavily tax everything going into or coming from igboland and may limit airspace permissions for flights. Students from igbo land will require visa to enter Nigeria and pay international school fees. No igbos will be employed or granted work visa anywhere in Nigeria for a very long time. Food imports and exports from the Igbo nation will face extreme taxation (or restrictions) from Nigeria so as to make it too expensive compared to other foreign imports. Forget ipob palm oil, it will be imported from Malaysia. Forget ipob yams and cassava, the Benue and Nasarawa farmers will be smiling to the banks. Food will be a problem in Igbo land and UN humanitarian aid may be the only lifeline as starvation sets in after only 8 months. That is if Nigeria does not block the UN aid provision in the first place. There will be an internal struggle for domination and leadership as clans, villages and kingdoms try to assert their influence in Igbo the new Igbo nation. Ipob will be subsumed in the struggle for power and may cease to exist. The person with the best-equipped militia will browbeat or assassinate opposition to install himself in power. So, a large proportion of the Igbo youths will be conscripted into rag tag armies, expendable pawns soon to be forgotten on the altar of selfish ambition. Over 500,000 of these youths will experience the horrors of violence, death, disease and hopelessness. A significant number will be scarred with psychological problems for life. Billions of Naira in closed Igbo businesses will jolt the Nigerian economy. However, the teeming masses of unemployed youths are ready to jump into the vacuum of what may be the world’s biggest employment jamboree of about 10 million jobs within 2 years. The Nigerian economy will jump-start and boast growth levels of 5% or more for five years or more. If the ipob engages the Nigerian Federation in a war; The Nigerian military will happily engage the ipob if they try to fight face to face and wantonly destroy to its hearts content as a lesson it was unable to teach the highly mobile bokoharam terrorists. World politics still strongly favors a Nigerian military solution. Putin has his hands full with the Middle East, Europe and the US tensions. Trump presidency still wobbles and fumbles its way forward. China has the Taiwan issue to contend with and will not interfere. Britain, France and Germany are also not interested in arming rebels or secessionist groups given the American experience in the Middle East and the cost involved. The religious card will not work because more Christians will still live in the rest of Nigeria (50 million) compared to the 40 million in the ipob nation. The rest of the world is fed up with providing funds and soldiers to be killed in quelling new conflicts. Furthermore, the huge investments by oil companies in the Niger Delta were inked with the Nigerian Government which still legal has locus standi as long as a government called federal government of Nigeria exists. The banks that gave loans to Nigeria will never stand by to watch all their money disappear. They will offer support openly or in secret to quell any conflict that goes against their interest. Hence, world opinion will favor a quick resolution with little loss of life. After which, they can then leave the Nigerian government the difficult and expensive task of rebuilding instead of funding it. Optimism about Israel intervention by Igbos is farfetched against world opinion which is barely in its favor right now. It may offer logistics quietly or train assassination teams for ipob. The assassination of Buhari which ipob had contemplated may not even favor the Igbo nation as the rampaging call for revenge by the North will drown any call for negotiation. It will be 1967 all over again with ipob as Nzeogwu et al. Any way you look at it. Its going to be a long bumpy ride for ipob and Igbo’s. They will need all the luck they can get. For the rest of us Nigerians I advise you say tearful goodbyes to your ipob/igbo friends, neighbors, and colleagues when they leave. They ignorantly follow a false prophet with false hopes to their deaths or a hell on earth. It is their choice unlike in 1967 when they were pushed to make the choice. Disclaimer: Don’t take what I wrote up there too seriously. They are just probabilities. 1 Like 1 Share |
A candid, concise exposition on on the contradictory nature of ASUU's demand. But this is just one facet of the many problems bedeviling Nigeria's public university system |
@seglad2 Click find my account. Then click: Request Google's help on the page that shows up. Hope you get it back. Best regards. |
Assalamu Alaikum to all. For some reason i am unable to reply to the original post so i am constrained to post this as a new topic. I wrote this with the intention of good. May Allah (SWT) forgive our omissions and commissions. My apologies in advance if i can not respond to comments that may arise: busy schedule. To clarify my perspective: The early generation did not have hospitals so all Muslims should stop using going to hospitals. The early generation did not use computers so all Muslims should not use them. The early generation did not ride cars so all Muslims should not use them. The early generation did not have formal schools nor were taught the sciences so all Muslims should abandon such and just learn the Quran and hadith solely. The early generation did not view television so all Muslims should not use them. The early generation never knew blood transfusion so all Muslims should avoid doing it. I hope everyone gets my drift. The problem is not Islam but all those half-baked sheiks churning out their warped illiterate concept of Islam which they presume should resemble the cultural experience of the early generation(e.g bokoharam easily comes to mind). Islam was meant to be a universal religion of obedience to Allah (SWT), valid for all times and all cultures. Islam has the fundamental view that all that Allah (SWT) had created has potential for good or evil excepting the Angels and those whom he has conferred His mercy (e.g Messengers and prophets). Allah's (SWT) laws regulate our actions, guide us from deviating and enacts punishments for those who err. To this end we have the Quran and Hadith for laws and guidance. The emphasis on what the early generation did or did not do, without basis in the Quran and Hadith, is a bid'ah if taken to the extreme. The actions of the early generation was governed by Islam as well as by their cultural ethos, so extrapolation of what was outside their experience should not be farcically interpreted negatively because they never could have imagined nor experienced it. Now to the opinion which i think the OP lifted from this sitesite without attribution. my Analysis: Jummah Mubarak is a form of greeting in Arabic and we know from Saheeh Bukhari: Volume 7, Book 62, Number 104: Narrated Al-Bara' bin 'Azib: The Prophet ordered us to do seven (things) and forbade us from seven. He ordered us to visit the patients, to follow the funeral procession, to reply to the sneezer (i.e., say to him, 'Yarhamuka-l-lah (May Allah bestow His Mercy upon you), if he says 'Al-hamdulillah' (Praise be to Allah), to help others to fulfill their oaths, to help the oppressed, to greet (whomever one should meet), and to accept the invitation (to a wedding banquet). He forbade us to wear golden rings, to use silver utensils, to use Mayathir (cushions of silk stuffed with cotton and placed under the rider on the saddle), the Qasiyya (linen clothes containing silk brought from an Egyptian town), the Istibraq (thick silk) and the Dibaj (another kind of silk). (See Hadith No. 539 and 753). Volume 7, Book 70, Number 553: Narrated Al-Bara bin Azib: Allah's Apostle ordered us to do seven things and forbade us to do seven other things. He forbade us to wear gold rings, silk, Dibaj, Istabriq, Qissy, and Maithara; and ordered us to accompany funeral processions, visit the sick and greet everybody. (See Hadith No. 104) And from Saheeh Muslim: Book 026, Number 5374: Abu Huraira reported Allah's Messenger (may peace be upon him) as saying: The rider should first greet the pedestrian, and the pedestrian the one who is seated and a small group should greet a larger group (with as-Salam-u-'Alaikum). We thus agree that Muslims are required to exchange greetings. The contention of the sheiks were that the Salam (As-Salam-u-'Alaikum) was the approved form of greeting, that Friday is an eid and it was not the action (custom) of the early generation to express such Jummah mubarak greeting on that day. The questions now are: Is doing so bad? Does doing so decrease Iman? Is doing so a good or bad deed? Does doing so violate any known law in Islam? Does doing so divide the Ummah or bring it together? Does doing so bring the Ummah to disrepute or impugn, debase or desecrate any tenet in Islam? Does Allah (SWT) forbid (haram) doing so? I believe the answers to this questions are obvious. Thus, Allah (SWT) has made the world wholesome for His Ummah excepting what He and His messenger (SAW) has ordered us to refrain from. Society will always evolve and new habits and trends will arise. Evaluating them from the view of the early generations is a retrogressive habit of most sheiks which is (to my opinion) responsible for the morass Muslims face in this age and time. Rather a conscientious body of rules on how this impact on the Ummah and how we may adapt it (Islamize it i.e. reject or accept) or we adapt to it (e.g. new scientific discoveries or health treatments) is pertinent for Allah (SWT) has not and did not place restrictions on our development. If he did we would still be living in the 3rd century and not have to deal with issues like: Is the greeting Jummah Mubarak halal? Allah (SWT) knows best. |
Here you go. Do not forget to write out a tutorial so that others may benefit from your experience. How To Recover Your Hacked Google/Gmail Account & Password In 5 Steps Gmail account recovery in 5 steps Best wishes. |
@duke2017 Your problem is a very old one with just one solution for now: specify the path of the opencv.dll library. Check this answer on stack overflow. It may help: System.loadLibrary(Core.NATIVE_LIBRARY_NAME) error Kindly post your work around so that others may benefit. Best wishes. |
@dorox10 Could not set up a tutorial so i got you two relevant links. Take a look at these two tutorials and complement with SPSS bundled help: 1. Import excel into SPSS Import Excel into SPSS 2. Scoring multiple choice questions in SPSS Score multi choice questions in SPSS The second link has applicable code which is clarified in the comments section. Doing same in Excel will require the use of string functions or writing VBA code. The choice is yours. However, based on the size of your data i may suggest excel. but if further statistical analysis of the data may be required, or you may need to add more data, then SPSS may be a more better choice. Best wishes. |
How to examine what you read for factual information (4) The era of disinformation is here. Disinformation refers to campaigns to saturate the info space with deceptive information with the intention of swaying public opinion or to achieve certain objectives. This implies that most of what you read on the internet and newspapers have been written to largely reflect interests which could be local, religious, tribal, regional, international or even psychological. The success of such disinformation campaign is evident in the large numbers of people (even on Nairaland) who believe everything served especially if it conforms to their emotional, religious, tribal or psychological prerogatives. So how can we distinguish between reality and fiction, facts and deceptions? This often depends on the level of knowledge and understanding of the content and language by the reader. The rules to apply are flexible and adaptable to all info space sources. Certain differences may be discerned when we look at political post but the technique is generally the same. In this and other posts (if I have the time) we shall look at how to interpret what we read for credible information and facts. Disclaimer: Any news article or post examined is for educational purposes only. I accept no liability from any action, loss or gain that may arise from using the skills or methods described in this post. Rights reserved Example 6 Post: Update On MPC Information on agenda/issues discussed and the attendance at the meeting- Note the mention of the volatile global economy and the current recession in the country. It is hinted that the meeting decision is subject to revision as the global and national economic outlook changes. 1 Key discussions- Impact of global economic outlook especially Brexit, US, EU and Asian political and economic environments, and crude markets. Highlights some recent economic policy decisions by central banks worldwide. External Developments Discussion on key economic fundamentals of the Nigerian economy- The MPC details its prognosis on the causes and effects of challenges currently faced and what it had achieved through its interventions (definitely little) and impacts on Nigeria's earnings, manufacturing, imports, debt profile and borrowing needs. It pointedly informs that power improvement depends on stoppage of pipeline vandalization and that improvements will be slow over the next 3 or more months. It recognizes the positive growth from agricultural production and informs that investments in non-oil is the big thing for economic recovery which attracts incentives and preferential capital funding by the government. The Committee is of the view that the key undercurrents i.e. scarcity of foreign exchange, low fiscal activity, high energy prices and the accumulation of salary arrears - cannot be directly ameliorated by monetary policy actions. The Committee hopes that the recent increase in oil prices would be complemented by production gains to provide the needed tailwinds to sustainable economic activity. Summary of its justification for decisions taken- It simply implies things will only get better if we produce made in Nigeria and buy made in Nigeria. It states reducing rates will increase inflation (more cheap money in circulation vs lower supply of goods), Reduce naira value, reduce investor confidence (their initial investment worth is reduced), cause forex instability (forex round tripping with cheap naira and also hoarding of dollars/speculation), and also affect the banking sector (stability/solvency). Lastly, the MPC hinted at a future decision to mop the extra currency pumped to inflate the economy in the current fiscal year (This points to confidence in a recovery or a measure to strengthen the naira). Also hinted is the existence of toxic debtors that may have to be managed to stabilize impacts on the economy. The Committee hopes that given the thrust of the 2017 budget and accompanying sectoral policies, output growth should resume in the short to medium term. The MPC, therefore, lends its voice to efforts for an early finalization of the 2017 Federal Budget by the authorities concerned, and the resolve to pursue a non-oil driven economy, as these will go a long way in stimulating aggregate demand and restoring confidence in the economy. The Committee also urged the authorities to seriously consider using the Public Private Partnership (PPP) model in its infrastructure development programme as a means of cushioning any possible shocks to budgeted revenue. MPC Decisions 4.0. The Committee’s Decisions |
How to examine what you read for factual information (3) The era of disinformation is here. Disinformation refers to campaigns to saturate the info space with deceptive information with the intention of swaying public opinion or to achieve certain objectives. This implies that most of what you read on the internet and newspapers have been written to largely reflect interests which could be local, religious, tribal, regional, international or even psychological. The success of such disinformation campaign is evident in the large numbers of people (even on Nairaland) who believe everything served especially if it conforms to their emotional, religious, tribal or psychological prerogatives. So how can we distinguish between reality and fiction, facts and deceptions? This often depends on the level of knowledge and understanding of the content and language by the reader. The rules to apply are flexible and adaptable to all info space sources. Certain differences may be discerned when we look at political post but the technique is generally the same. In this and other posts (if I have the time) we shall look at how to interpret what we read for credible information and facts. Disclaimer: Any news article or post examined is for educational purposes only. I accept no liability from any action, loss or gain that may arise from using the skills or methods described in this post. Rights reserved Example 4 News: Rivers police arraign 45 Pro-Biafran agitators for treason Journalistic summary of the news- Hint: Note the subtle attempt to confer legitimacy on IPOB and MASSOB by mentioning them together with the police whereas they are unregistered/proscribed bodies unknown to Nigerian law. It also describes what happened as an 'agitation', but for what? The Rivers State Police Command yesterday arraigned 45 members of the Indigenous People of Biafra, IPOB, and the Movement for the Actualisation of Sovereign State of Biafra, MASSOB, before two Chief Magistrate Courts sitting in Port Harcourt for treason over their alleged involvement in the Friday agitation in Rivers State. Fact- A rally was organised but the news blames the police outright without presenting us with accounts from both sides as to what transpired. Hint: Note the use of the word 'America', 'solidarity' and 'rally' with the unregistered/proscribed members implying peace and the association of 'disrupted' with the police before even presenting the reason of 'no permit'. It then unthinkingly labelled the members as 'Pro-Biafran agitators' which leans towards the treason allegation. The issue of permit and treason are very different and the reportage seems confused on which it thinks is applicable. Interestingly, the police arrested 65 before disrupting the rally. We need a video reportage, not clip, from beginning to end so we can make a good judgement of what happened at the rally. The members of the IPOB and the MASSOB had on Friday, organised a solidarity rally to commemorate the swearing in of Mr Donald Trump as the new American president. Fact- Verifiable information based on court proceedings. Note the reportage now substantiates the treason offence by quoting copiously from the court proceedings. The rest of the reportage is about court processes in dispensing justice which looks very slow. Hint: Note the charges under state and federal laws and the words 'conspire amongst yourselves to commit felony', 'treasonable felony', 'displaying flags and other items of the Biafran Republic', 'take over the government of Nigeria by force'. This are serious charges if they can be proved in court. Unless there is information to the contrary it seems the issue of treason and not rally permit seems valid here. The Commissioner of Police in the state, Mr. Francis Odesanya charged the arrested persons to court on two counts of conspiracy to felony and treasonable felony. Verdict: The news is cleverly written to pander to a dual readership. The first part confuses the gullible while the latter part correctly presents verifiable information on the official reaction to what happened. We only know a rally held and 65 were arrested and charged with serious offences. As to what really happened, little information is provided and we are given the choice of police suppression or violation of Nigerian laws as a causative reason. The reader is left to speculate or conclude based on his preconceptions or leanings. Example 5 News: Reps summon Kachikwu, GMD NNPC, NPA over petrol pump price Journalistic summary of the news- The emphasis on who was invited and the words 'the need to review the pump price of fuel'. This subtly implies fuel prices must be reviewed. Note that unlike ia obtainable in America, Nigeria's legislature resolutions have no power unless it is enacted by both upper and lower chambers. THE House of Representatives Ad-hoc Committee on review of petroleum pump price, yesterday, summoned the Minister of State for Petroleum, Dr Ibe Kachikwu; Group Managing Director of the Nigerian National Petroleum Corporation, NNPC, and Managing Director of the Nigerian Ports Authority, NPA, to appear before it on the need to review the pump price of fuel. Speculation- A simple price analysis would have been more effective instead of verbal pleadings of the unions to the House committee not to allow an increase because it is 'not the right time' and because of dollar payments to Government agencies. No extra information is provided and readers are required to believe this without any attempt at economic analysis of what is going on. This came as Nigerian Union of Petroleum and Natural Gas Workers, NUPENG, and its Petroleum and Natural Gas Senior Staff Association of Nigeria, PENGASSAN, counterpart, told the committee that on no account should marketers be allowed to increase the pump price of petrol, saying “this is not the right time to review the pricing template of PMS.” Speculation- Which stakeholders? Still no price analysis to convince readers. Hint: Note the emotive allusion to the suffering of Nigerians as a cogent reason. Similarly, some stakeholders at the public hearing, including some lawmakers, were of the opinion that the current pump price was too high and that it should be brought down to ameliorate the sufferings of Nigerians. Speculation- Hint: Note the subtle tribal wargames begin Igbo vs Hausa/Fulani. The reportage gives no proofs rather than state the allegation and playing on the emotive issue of suffering Nigerians. The Raphael Nnanna Igbokwe-led Ad-hoc committee in the two-day public hearing had accused a number of government agencies of contributing to the astronomical price of petrol, which is currently causing Nigerians pains. Falsehood- Ports the world over charge berthing ships depending on cargo. So, if 84 kobo/litre is abolished we get a reduction of what on each litre. Something does not add up. A quick check of the internet shows NPA has been collecting 45 - 84 kobo on each liter since 2011. Is this an attempt to deprive the nation of revenue or a genuine attempt to give Nigerians much needed relieve? The lawmakers said the NPA was not doing enough to justify the 84 kobo/litre collected from importers, adding that NPA would not have been able to justify the amount it was collecting if the seas were dredged and vessels not engaged on ship-to-ship discharging of products that add to costs of products and loss of revenue for the country. Unethical- Hint: Note the house seems to be in a permanent battle of supremacy and control over heads of government agencies with its limited powers. This smacks of incompetence. The focus should have been on which information was provided and which was not provided. Igbokwe, who represents Ahiazu Mbaise/Ezinihitte federal constituency of Imo State, insisted that the MD of NPA must attend today’s public hearing, saying the Acting General Manager, Mr. Ephraim Okoro, who represented him, lacked the capacity to answer all the questions of the committee. Fact- As presented by the PPPRA. Hint: note that nothing was said on how reducing or abolishing the 30 kobo charge by the PPPRA will benefit Nigerians or the 84 kobo charge by the NPA. On its part, Petroleum Products Prices Regulatory Agency, PPPRA, represented by its Executive Secretary, Victor Shidok, told the committee that the 30 kobo administrative charge on petrol was for services such as data capturing and monitoring by staff deployed to depots across the country. Whoa- The committee will now perform the functions of an auditor. What stops it from ordering an audit so that it can focus on other important issues. Where is the annual audit report from the auditor general? But what about the legislature budget audit for the last few years since it can now do audits. Seems the committee is patronizing Nigerians. The committee, however, insisted that the agency must present its list of inspectors engaged from 2012 till date, amounts paid, copies of agreements entered into with them and proof of payment Verdict: The news informs of a house committee investigation into a rumored fuel price increase. It provides no proof of the increase and subtly attributes the price increase to the 84 and 30 kobo charge by governmental agencies. It ignores the unstable price of the dollar and the corrupt practices of the fuel importers in its reportage. It also propagates ignorance rather than educate readership by not presenting a simple price analysis but rather blaming government and its agencies. This piece is not news but a disguised anti-government write-up for readers to speculate on. |
How to examine what you read for factual information (2) The era of disinformation is here. Disinformation refers to campaigns to saturate the info space with deceptive information with the intention of swaying public opinion or to achieve certain objectives. This implies that most of what you read on the internet and newspapers have been written to largely reflect interests which could be local, religious, tribal, regional, international or even psychological. The success of such disinformation campaign is evident in the large numbers of people (even on Nairaland) who believe everything served especially if it conforms to their emotional, religious, tribal or psychological prerogatives. So how can we distinguish between reality and fiction, facts and deceptions? This often depends on the level of knowledge and understanding of the content and language by the reader. The rules to apply are flexible and adaptable to all info space sources. Certain differences may be discerned when we look at political post but the technique is generally the same. In this and other posts (if I have the time) we shall look at how to interpret what we read for credible information and facts. Disclaimer: Any news article or post examined is for educational purposes only. I accept no liability from any action, loss or gain that may arise from using the skills or methods described in this post. Example 3 News: Accused of clampdown, Buhari says he’s proud of Nigerian media Journalistic summary of the news- Hint: President's Twitter handle mentioned as source for verification President Muhammadu Buhari has saluted the Nigerian media, saying journalists have performed their duties diligently. Fact- Hint: It was reported that he wrote the National Assembly on transfer of executive powers to the VP while away Mr. Buhari left last week for the United Kingdom for a vacation. Interesting- Portrays the President as a person who has an ear to the news despite being on holiday. But given the current hardship in the country one may question this. The picture however shows a man with no health issues with a tea or coffee pot by his side. The sitting position is a psychological comfort/dominant pose over his environment which is generally an unconscious unisex rest action. The mention of Channels TV may be just to prove a point(Hint- Fayose) or due to the limited availability of Nigerian cable TV stations abroad. President Buhari, whose picture was also posted in the tweet, specifically named Channels TV as one of his favorite television stations. Fact- Hint; Flight plans are submitted 24 hrs before a flight. Anybody could have checked the Presidents flight destination after it had landed if you are web savvy. However, Premium Times did not indicate if they did this. This implies they are aware of this information or believe the spokesperson. The presidency, on Saturday, denied reports suggesting Mr. Buhari had taken seriously ill or even passed away. A subtle accusation of press gagging against the President- Hint: The case reported was between Tukur Buratai and Premium Times. But here we are asked to consider the involvement of the President. OK, present factual evidence so i can form my judgement. The president’s tweet is seen as aimed at dispelling rumors about his health, while also reassuring the public of his government’s relationship with the media. Fact- Hint: Its in the President's letter to the house President Buhari left Abuja for the UK on Thursday. He is expected to resume work on Feb. 6, 2017. Verdict: The news reliably informs that the president is not troubled by any life threatening or debilitating disease. It correctly identifies the tweet as an attempt to placate the recent clampdown on the press by the police. It however, subtly tries to create the impression without further proof, that the Presidency may be involved in the clampdown despite its own report about the issues. 1 Like |
How to examine what you read for factual information (1) The era of disinformation is here. Disinformation refers to campaigns to saturate the info space with deceptive information with the intention of swaying public opinion or to achieve certain objectives. This implies that most of what you read on the internet and newspapers have been written to largely reflect interests which could be local, religious, tribal, regional, international or even psychological. The success of such disinformation campaign is evident in the large numbers of people (even on Nairaland) who beleive everything served especially if it conforms to their emotional, religious, tribal or psychological perogatives. So how can we distinguish between reality and fiction, facts and deceptions? This often depends on the level of knowledge and understanding of the content and language by the reader. The rules to apply are flexible and adaptable to all info space sources. Certain differences may be discerned when we look at political post but the technique is generally the same. In this and other posts (if I have the time) we shall look at how to interpret what we read for credible information and facts. For starters, here are two to whet your appetite. Disclaimer: Any news article or post examined is for educational purposes only. I accept no liability from any action, loss or gain that may arise from using the skills or methods described in this post. P.S.: My replies may be slow in coming. Rights reserved. Example 1 Post: Nigerian Diplomat’s Son Jailed For Raping & Murdering A Nigerian Sex Worker Verifiable but extra information needed- hint: full name and also father is a government worker Bala Chinda was sent by his father, an immigration attache to the Nigerian embassy in China, to study at the Robert Gordon University in Aberdeen, Scotland. Verifiable but extra information needed- hint: crime committed but in which specific area. Note the racial profiling to counter the name dropping (Jessica McGraa). But only few weeks into his stay, the 26-year-old would have his life derailed in ways that he or his parents could not have imagined. He was found guilty of raping and murdering 37-year-old Jessica McGraa, a sex worker who also happened to be Nigerian. Which court? - Hint: The story is incomplete despite reference to court proceedings. Law enforcement involved (good), but motive presented weak. The court heard throughout the trial that Chinda had been desperate for sex on the evening before and the morning of McGraa’s death. After searching for prostitutes and brothels nearby he eventually ended up meeting his victim at her a residence. Unfortunately, he did not have the cash required for the sexual transaction and killed her in a frustrated rage. According to court papers, Chinda then stole McGraa’s mobile phones in order to dispose of any evidence linking him to her. Are you kidding me- Hint: smother and rape her at the same time, questionable? Note smothered and strangled are almost same in meaning. Printers devil or tabloid journalism? It is believed that he smothered her with a pillow as he raped her and strangled her afterwards with a scarf. Gossip- Hint: Speculation about the deceased lifestyle, no respect. Sign of tabloid journalism Jessica McGraa was said to be a Nigerian orphan whose career as a sex worker was unknown to her friends and family who thought she sold hair extensions. Her fee was up to £1800 per night. She is survived by a young son, an ex-husband and a 21-year-old boyfriend who both did not know of her other life until the murder. Verdict: The news as written informs of a real crime successfully prosecuted in a court but also tries to profile Nigerians as criminally and morally debased. Also it is lacking in information to make it a basis for anything other than conversation and more speculation. Example 2 News: Corruption: UK Gets Evidence Against Diezani Speculation- Hint: Not verifiable unless if the UK says or gives more information The United Kingdom (UK) is now in possession of a pile of evidence against former Minister of Petroleum Resources, Mrs. Diezani Alison-Madueke, courtesy of the Economic and Financial Crimes Commission (EFCC). Speculation- Hint: information is not verifiable without more information A team of EFCC detectives was on standby yesterday to proceed to London to interrogate the ex-minister. Something is definitely going on- Hint: Was Magu in London? If yes, then something which may or may not be related to the Diezani case is heating up. Note that London crime agencies don’t call country head agencies for meetings unless it is a high-level affair and also because of need for secrecy and negotiation over details or evidence. Sources familiar with her investigation by the EFCC told The Nation that all the evidence gathered by the anti-graft agency on Diezani had been handed over to UK investigators. The Acting Chairman of the EFCC, Mr. Ibrahim Magu accompanied by some detectives took the evidence to the National Crime Agency in the UK. “The evidence includes an inventory of more than 15 choice properties at home and abroad, her account status, documents and vital video clips,” the source said. “The evidence was taken to London in preparation for her trial. Speculation- Hint: Is she really recovered? Can we verify this? “We learnt that she has substantially ‘recovered’ and we want our team to interview her in London. Speculation- Hint: Something related to the Diezani case is up “When the trial begins, Nigerians will have a full insight into our findings against the ex-minister.” Fact- Hint: this was verified by EFCC itself. Continuing, the EFCC source said: “We have placed some of these properties under temporary asset forfeiture. We are still investigating some properties allegedly bought by the ex-minister through some proxies. Partly true- Hint; Bribery scandal substantiated but still not proven in courts yet. But only two RECs (one is Rivers) were reported to have confessed on being shown videos. Name the politicians please. “On the $115million poll bribery scandal, we have video clips of how electoral officials and politicians were hauling cash from banking halls. Opinion- Hint: Wants us to judge EFCC based on outcome of trial judgements. This reflects confidence in evidence against accused-very interesting EFCC does not engage in a personal vendetta. Nigerians will know the truth at the end of the trial either in Nigeria or in the UK.” Verdict: It is probable that evidence may have been shared but the story is all about increased activity regarding the Diezani case in the near future both here in Nigeria and in the UK. The news is based on few facts and it wants us to believe information from its source which could be mere speculation. What happens in the near future will determine the credibility of the source? For now, news assures us to expect more on the case and that the suspect is cooked goose (mind the pun). |
Credits:Ghacks website Microsoft Director of Sales Excellence - Eric Ligman wrote on his blog page that Microsoft is giving away hundreds of free ebooks currently covering a wide variety of topics that include Windows, Azure, Office, Windows Server, and SharePoint among others. The giveaway features recent publications as well as older ones. The Windows category for instance lists 14 ebooks covering Windows 10, among them "Introducing Windows 10 for IT Professionals", "Deploying Windows 10: Automating deployment by using System Center Configuration Manager" and "Upgrading to Windows 10: A simple hands-on guide for everyone". Not all publications offered for free are full-blown ebooks with hundreds of pages though. Many are, but there is also a good selection of shorter publications, for instance the one-page PDF file that compares security features of Windows 7 with those of Windows 10. Most ebooks are designed for IT professionals, administrators and business/Enterprise use. While that is the case, some are without doubt useful for home users as well. Many ebooks are offered in several formats, with PDF, EPUB and DOCX the most common formats. You will find the occasional MOBI format thrown in but that is about it. All ebooks are completely free which means that they don't have an expiration date associated with them. One issue that you may run into however is that there is no "download all" button available that works. While there is a download all button displayed, it lists to a FAQ page that reveals why there is no such download option. Free ebook selection The following list provides you with a sample listing. All ebooks listed below are offered as downloads on the MSDN website. Introducing Windows 10 for IT Professionals Windows 10 IT Pro Essentials Top 10 Tools Introducing Microsoft Power BI Microsoft Azure Essentials Fundamentals of Azure Microsoft Azure Essentials Azure Machine Learning Microsoft Azure Essentials Azure Automation Introducing Windows Azure™ for IT Professionals Microsoft® Office 365: Connect and Collaborate Virtually Anywhere, Anytime Introducing Windows Server 2016 Technical Preview SharePoint Server 2016 Reviewer’s Guide SharePoint Server 2016 Quick Start Guide for Single Server Farms Introducing Microsoft SQL Server 2016: Mission-Critical Applications, Deeper Insights, Hyperscale Cloud, Preview 2 Windows Powershell 4.0 Examples Quick Guide WINDOWS POWERSHELL 4.0 LANGUAGE QUICK REFERENCE Programming Windows Store Apps with HTML, CSS, and JavaScript, Second Edition The selection includes quite a few quick reference sheets for various Microsoft products. It is unclear for how long these ebooks will be offered for download, so grab them as quickly as you can before they are pulled again. For the techies, the attached text file contains links to all the free ebooks. I recommend Jdownloader to download all the links automatically.
|
Source credit: Kieren McCarthy ICANN Knifes Africa's Internet: Axes Nine $185,000 Domains California-based ICANN, which has faced repeated criticism for its failure to reach beyond a North American audience, saw just 17 applications from Africa out of just over 1,900 applications for new dot-word domains back in 2012. Of those 17, nine this week received termination notices from ICANN, despite them having paid $185,000 for the right to their dot-names and having run through an evaluation and contract process. The applicants for .naspers, .supersport, .mzansimagic, .mnet, .kyknet, .africamagic, .multichoice, .dstv and .gotv – all based in South Africa – signed contracts with ICANN in 2015 but failed to put their generic top-level domains live within a 12-month window. As a result, ICANN is now rescinding their rights. The only company from Africa that has successful put new top-level domains online is the registry operator for South Africa's .za, ZACR, which applied for and runs three city TLDs: .capetown, .durban and .joburg. Meanwhile, ICANN is in active dispute with the biggest application from Africa: .africa. One of the two applicants for the name, DCA Trust, is suing ICANN in a Los Angeles court for running a sham process in which it attempted to hand over the name to its preferred bidder, ZACR. 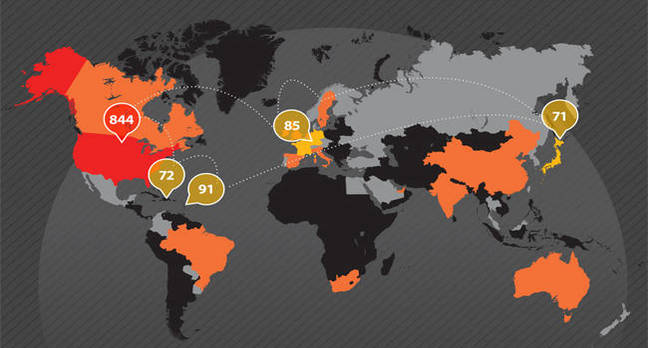 Domain-name overseer ICANN has killed off the majority of Africa's new internet. Trust issues DCA Trust has already won an independent appeal against ICANN in which the organization was found to have broken its own bylaws. Documents from that case revealed ICANN's staff had actively interfered with the process to ensure that their preferred bidder won, then sought to cover up their involvement and then knowingly misled people about the coverup. Last month, an injunction was filed against ICANN after it attempted for a second time to hand the .africa domain to ZACR despite the ongoing legal fight. ICANN has until today to file a response to DCA Trust's allegations. Of the remaining three applications from Africa, one has been withdrawn and the other two have until November to put their names live or they face the same fate. Dot-brand to dot-banned Last month, ICANN warned more than 200 companies that it will kill off their rights to new top-level domains if they didn't put them live on the internet. The majority were big brands, including Intel, Netflix, Lego and Nike which paid for the rights to their dot-brand name but have no current plans to use them. Most don't wish to cover the cost of putting the names live or to start paying ICANN's annual fees. It was perhaps unfortunate that of the first 10 termination notices than ICANN has sent out, nine of them come from Africa. The self-absorbed DNS overseer was heavily criticized when it rolled out its "new gTLD" program for failing to communicate its plans beyond the mostly North American audience that attends its conferences. Of the 1,930 applications, 844 came from the United States. A further 150 or so came from US organizations based in offshore tax havens such as the British Virgin Islands and the Cayman Islands. In response, the organization launched a belated "applicant support program" and set aside $2m to fund it. But again, it failed to communicate the program's existence to people outside its own halls. As a result, the program received just three applications, two of which were rejected for not meeting the criteria. |
Apple Recycles Old Iphones And Recovers $40 Million In Gold  Apple released its latest annual environmental report yesterday, and some of the numbers included reveal just how much the company is able to recover from old devices. Business Insider notes that Apple was able to recover over 61 million pounds of steel, aluminum, glass, and other materials from its computers and iPhones. Included in that total is 2,204 pounds of gold, which is well over a ton. Apple released its latest annual environmental report yesterday, and some of the numbers included reveal just how much the company is able to recover from old devices. Business Insider notes that Apple was able to recover over 61 million pounds of steel, aluminum, glass, and other materials from its computers and iPhones. Included in that total is 2,204 pounds of gold, which is well over a ton. The gold haul alone is worth $40 million at current prices ($1,229.80 per troy ounce of gold), while the total amount of material recovered is reportedly worth well over $50 million. Cult of Mac ran the figures quoted by Apple through today's metal prices, and came up with individual figures for copper ($6.4 million), aluminum ($3.2 million), silver ($1.6 million), nickel ($160,426), zinc ($109,503), and lead ($33,999).  Apple says in total it collected almost 90 million pounds of ewaste through its recycling programs, which works out as 71 percent of the total weight of the products the company sold seven years earlier. Apple made much of its efforts to reduce waste at its media event last month. The company also unveiled a robotic system it has developed called 'Liam' that can disassemble old iPhones and recover recyclable materials. The company said that Liam will initially focus on recycling junked iPhone 6 handsets, but Apple plans to modify and expand the system to deconstruct different models and recover more resources. Source |
Babies May accept Bribe to Abandon Their Morals Even early in life, people show distaste for rule-breakers and wrongdoers. Past research has shown that kids will refuse to help or will even shun someone who’s behaved badly. “As young as three months, babies are showing these preferences for prosocial over antisocial characters,” says Arber Tasimi, a Ph.D. candidate at Yale. But a recent study by Tasimi, published in the journal Cognition, found that kids — even babies! — will abandon those principles if the payoff’s good enough. Kids don’t just parallel adults in their recognition of moral and amoral behavior — they’re also like us, it seems, in their willingness to become more morally flexible for the right price. And it starts at a young age. In the first experiment, Tasimi and his co-author took a group of kids between the ages of 5 and 8 and showed them photos of two characters named Max and Craig. In some cases, all the kids knew about the characters was that Craig had more stickers to give away than Max did. (These kids tended to choose Craig’s stickers over Max’s.) In other cases, the researchers gave them a bit more background on their personalities: ‘‘Craig is always mean. The other day, he hit someone on the playground … Max is always nice. The other day, he hugged someone on the playground.” Across all ages, when the choice was one sticker versus two, the kids in the second group tended to go with the one from Max — seemingly out of a desire not to take stickers from the morally sullied Craig. When the choice was one versus four or one versus eight, they were pretty evenly split. But when it came to one versus 16, the majority went with the bigger haul, even if it came from the jerk. The caveat: The study authors weren’t sure if the kids were truly acting according to their own desires, or if they were trying to please the experimenters by making the seemingly right choice — an infant version of the so-called social desirability bias. (As the study notes, kids start thinking about how other people perceive them sometime between age 3 and age 5.) You know what type of person doesn’t care about protecting their rep, though? A baby. Surely babies, innocent creatures that they are, would stay on the side of good over evil? Nope. When Tasimi and his colleagues ran a similar experiment on babies, the babies sold out, too. In the second experiment, 64 infants between 12 and 13 months old were assigned to one of two conditions. Members of the control group were introduced to two puppets offering different amounts of crackers, and they reliably opted for the bigger serving (there were no indications that one puppet was “better” than the other). In the second group, the puppets put on a show: While one puppet struggled to open a box, another either lent a hand or made things harder by slamming the box shut. In the subsequent cracker test, the babies who had seen the show followed roughly the same pattern as the older kids. They’d accept crackers from the nice puppet over the mean one if the choice was one versus two. “They’re going against their baseline desire for more,” Tasimi says. “I take it as evidence of, ‘I’m rejecting your offer because I don’t like what you did, even though it’s a costly choice on my part.’” But if it was one versus eight, they tended to accept the bigger bounty of the mean puppet. “When the stakes are modest, children show a strong tendency to go against their baseline desire to optimize gain to avoid ‘doing business’ with a wrongdoer,” the study reads. “However, when the stakes are high, children show more willingness to ‘deal with the devil.’” Source |
2016 has broken 135 year global temperature records as global warming increases The past 11 months have been the hottest such months in 135 years of recordkeeping, a streak that has itself set a record and puts in clear terms just how much the planet has warmed due to the buildup of greenhouse gases in the atmosphere. New global temperature data released on Friday by NASA put March at 2.3°F (1.28°C) above the 1951-1980 average for the month, making it the warmest March on record. It beat out the previous warmest March, from 2010, by 0.65°F (0.36°C)—a handy margin. It also marked the 11th month in a row to set such a record, beating out the previous such streak of 10 months set back in 1944. March also marked six straight months with temperatures that were more than 1°C above average, a notable mark given the stated goal of international climate talks to keep warming in the 21st century below 2°C (with some talk of even aiming for 1.5°C).  March wasn’t as anomalously warm as February, which retains its title as the most anomalously warm month on record. (January 2016 had previously held the number one position.) Several other agencies around the world keep their own global temperature records, including the National Oceanic and Atmospheric Administration, which will release its March numbers next Tuesday. So far this year, the NOAA and NASA data has tracked fairly closely. The Japan Meteorological Agency put March at 1.93°F (1.07°C) above the 20th century average. Each agency uses different baselines and their numbers can differ slightly from each other because of different ways of processing the temperature data. For the last few months, global temperatures have received a boost from an exceptionally strong El Niño, but the bulk of the temperature rise is due to the excess heat trapped in the atmosphere by carbon dioxide and other greenhouse gases emitted by human activities. The succession of temperature records has also been accompanied by other notable climate records, including thebiggest ever year-to-year jump in carbon dioxide levels at the Mauna Loa observatory in Hawaii, as well as a record low winter Arctic sea ice peak. The Arctic, in fact, has been one of the most anomalously warm areas of the planet over the past year and is warming at twice the rate of the planet as a whole. So far, 2016 is on track to beat out 2015 as the warmest year on record, but the year is only three months old. El Niño is waning, and it could usher in a La Niña later in the year, which tends to have a cooling effect on global temperatures. But how much of a role any La Niña plays will depend on how strong it is and when it forms and it is likely to have more of an influence on 2017’s temperatures than this year’s. Source |
There is the need to make clarifications on the rumours of JAMB grade markups, result swapping and so on. I have listened with amusement to some Jambitos making uneducated assertions and was aghast to hear how they unbundled their (and also parents') hard earned money to pay for modification to the outcomes of JAMB CBT's. Many can attest that such efforts have ended in regret and angry recriminations and accusations. The fact is that any manipulation is not readily possible at the CBT centre. Unless the proposed JAMB CBT system has been modified, the original proposal has several security features. The not so technical features involves: 1. The setting of five or more different sets of questions for each subject. 2. Each question has a unique ID so that it can be identified. 2. The CBT test server has the ability to serve combinations of such questions so that the possibility of two candidates in the same centre having the same set of questions for the same subject is slim. I.e Maths questions on system A are different in both form, type and numbering from that on system B - similar to paper type on the written tests. 3. Also the possibility of two candidates having the same set of questions for the same subject combination is low. I.e Maths,Eng and Geo questions on system A are, 50% or more, different in both form, type and numbering from that on system B. 4. The CBT server records each candidates response in its database together with the question ID. 5. Finally, the results processing involves the transmittance of the database to JAMB for processing which then issues the results. Thus it is obvious that manipulation is almost impossible either from the JAMB or CBT centre end. Many might argue that gaming the system is possible if: 1. The CBT centre has the skill or resources to prise all CBT questions out of the CBT server database and give favored candidates all of the CBT questions before hand which will run into pages of paper. 2. The CBT centre has the skill or resources to log into the CBT server database and manipulate the response of a candidate to the test questions. 3. Or if a JAMB staff in the IT section, or higher, with administrative access to the results database is suborned. Be advised that JAMB has taken all such scenario into consideration and the other technical features and guards (not discussed here) have been implemented to discourage such sabotage. So be informed and do not fall for scam proposals to change results in any way. DISCLAIMER: I do not work for JAMB or its affiliates but do have requisite experience in the design and implementation of such systems. Apologies for the inability to take questions. TheArbiter |
How our brains work on caffeine  A mug of cofee  Roasted coffee beans It runs through our bodies on a regular basis, either through coffee or tea, and it has become an embedded morning habit for many of us! An average person in the United States consumes approximately 300mg per day, which is equivalent to three to four cups of coffee, and over 90 percent of the world’s population ingests some form of caffeine. To give you an idea of how caffeine levels of coffee compared to other substances: 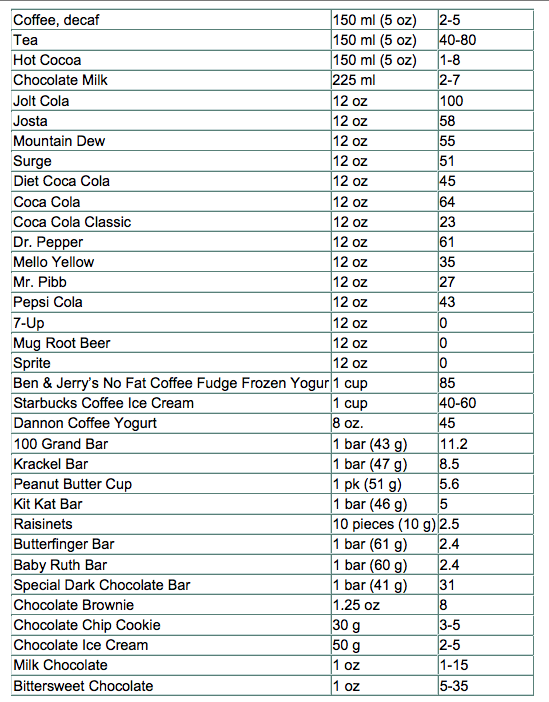 Caffeine has become so popular, that today there are energy drinks, gum, beef jerky, and other unimaginable products in stores that promises shoppers the boost the need to get through their day. So let’s uncover how our brain works on caffeine. There have been many studies and research papers that have gone back and forth that support the benefits and negative impacts of consuming caffeine on a regular basis. With all this information thrown at us, it’s easy to feel overwhelmed and confused. Before we dig deeper into how our brain works on caffeine, let’s first understand how caffeine works. How caffeine works Caffeine in simple terms is a compound that is found in over 60 different plants around the world including cacao pods, tea leaves, and kola nuts. What is particularly interesting about caffeine is that chemical relatives of caffeine exists all around our bodies. Every moment that you’re awake, the neurons in your brain are firing away. As those neurons fire, they produce adenosine as a byproduct, and your nervous system is actively monitoring adenosine levels through receptors. We often get tired at the end of the day because adenosine levels reach a certain point in our brain and spain cords, especially when we’re learning something new. Given the similarities of size and shape of the caffeine molecule and adenosine molecule, your body accepts it as an equal replacement, as it heads right for the adenosine receptors in your system. 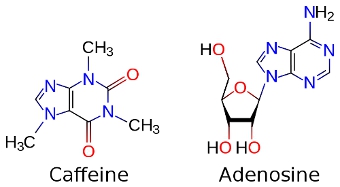 With those receptors replaced and blocked, the brain’s own stimulants, dopamine and glutamate, can do their work more freely without distraction, giving you more stimulated energy. While the extra energy is great for those of us who need a bost, it’s not all good for our brains. *Disclaimar: Every side effects (good or bad) mentioned here will vary from person to person, and we recommend you use the following as a guideline to making better decisions. Common downsides of coffee 1. Trouble sleeping We’ve all had nights where we roll side to side of our beds because we just couldn’t fall asleep. While it’s perfectly fine to have our dose of caffeine in the morning, we should be cautious of consuming it in the later parts of the day, especially if you’re sensitive to caffeine or an early sleeper. So until when is it safe to drink caffeine that will have little to no affect on your sleep quality? According to the Journal of Clinical Sleep Medicine, six hours before sleep is the recommended deadline to follow of when you should stop consuming more caffeine. 2. Energy crashes Unless you are drinking coffee or taking a caffeine stimulant on a regular basis, it’s common to experience a crash in our bodies after the energy boost wears off. That’s because caffeine initially stimulates your body to produce more adrenaline and dopamine than usual, two substances in your body that contribute to energy and positive mood; when these chemicals begin to drop again, you can experience fading energy and a drop in mood. A strategy that has been proven by researchers is to drink their coffee in strategic times, such as a caffeine nap. Here’s what Wired has to say about caffeine naps, its effects and how to use it to your advantage: Experiments performed at Loughborough University in the UK showed that the sleep-deprived need only a cup of coffee and 15 minutes of shut-eye to feel amazingly refreshed. 1. Right before you crash, down a cup of java. The caffeine has to travel through your gastro-intestinal tract, giving you time to nap before it kicks in. 2. Close your eyes and relax. Even if you only doze, you’ll get what’s known as effective microsleep, or momentary lapses of wakefulness. 3. Limit your nap to 15 minutes. A half hour can lead to sleep inertia, or the spinning down of the brain’s prefrontal cortex, which handles functions like judgment. This gray matter can take 30 minutes to reboot. 3. Heart burn or upset stomach The majority of our bodies are contained by water. We need it to feel energized, be healthy, and simply survive. Caffeine however, triggers our bodies to remove water from our bodies, making us feel dehydrated. It also raises the amount of acid in our stomach, causing heartburn or upset stomach. While these are the common downsides of caffeine, here’s an infographic displaying some of the other possible symptoms. 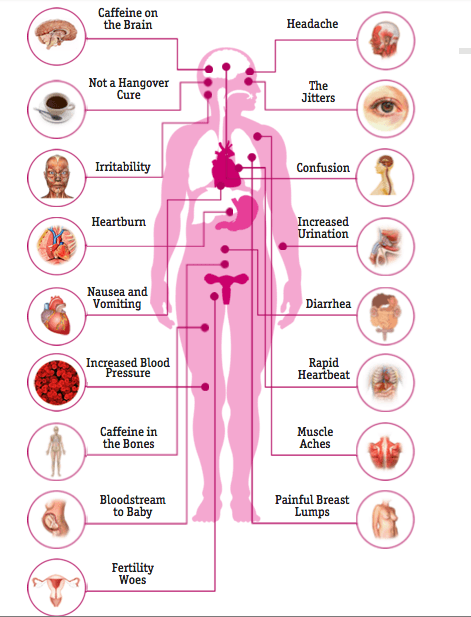 Side effects of coffee Now that we’re done with the pessimistic side of caffeine, let’s talk about the beauty that caffeine can bring us. Positive effects of coffee 1. Burn fat The great thing about coffee is its low calorie intake. A regular black coffee will contain only two calories (without the sugar and cream). In fact, several studies show that caffeine can boost the metabolic rate by three to 11 percent, which is why almost any weight loss product you’ll see on the store shelves will contain some levels of caffeine inside. Keep in mind that this powerful effect will not be sustained for long-term coffee drinkers. 2. Nutrients for your body Unless you’re drinking instant coffee, the coffee beans to make the coffee contain nutrients that are recommended for our daily intake. A single cup of coffee contains: Riboflavin (Vitamin B2): 11 percent of the RDA. Pantothenic Acid (Vitamin B5): six percent of the RDA. Manganese and Potassium: three percent of the RDA. Magnesium and Niacin (B3): two percent of the RDA. Coffee also contains one of the highest sources of antioxidants for our bodies. Americans get more of their antioxidants from coffee than any other dietary source. Nothing else comes close. – Joe Vinson, Ph.D 3. Reduce risk of diseases From diabetes, dementia, Parkinson, to Alzheimer’s disease, coffee drinkers have a much lower risk of having these diseases in the future. Several studies show that coffee drinkers have: up to a 65 percent lower risk of getting Alzheimer’s disease a much lower risk of developing Parkinson’s disease, with a reduction in risk ranging from 32 to 60 percent a 23 to 50 percent lower risk of getting diabetes up to a 40 percent lower risk of liver cancer a 15 percent lower risk of colorectal cancer (those who drank four to five cups/day) 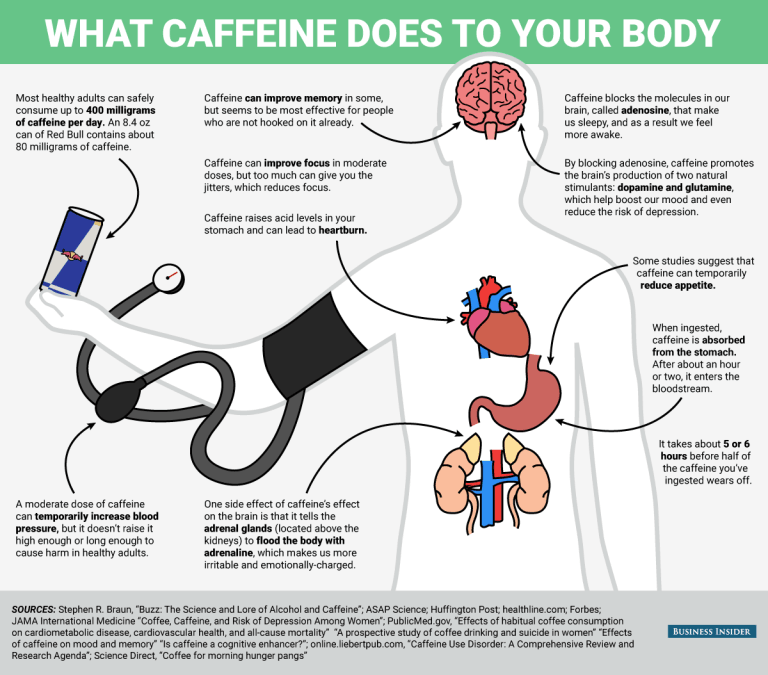 Source 11 Likes 6 Shares |
The Hinatuan River is a river on the island of Mindanao in the Philippines. It flows into the Pacific Ocean at Hinatuan, Surigao del Sur. The River is also referred to as the “Enchanted River” by many locals and tourists. Nicknamed the Enchanted River because of its unknown beginnings – starts from a 80 feet deep spring. It is called the “Enchanted River” because the water seems to magically flow without any source, as well as being so deep and blue. It is considered one of the most beautiful tourist attractions in the Philippines.  Due to its close proximity to the sea, some believe the idyll was created when seawater flowed through long tunnels and caverns deep below the ground, finally resurfacing at the spring – which is 80 feet deep in areas. With its tranquil blue waters, palm trees and rock pools, this idyllic river in the Philippines is nothing short of paradise. The 80 feet deep waters are popular with sunbathers, swimmers and those who wish to practice their diving skills.  With numerous fishes and other creatures living in its deep waters, the area is popular with snorkelers as well as divers and explorers. Moreover, locals share that nobody has been successful in catching the fish in this river, whether by hand or by spear. They say its bluish color is a result of its depth and the water clarity changes throughout the day. At around 12:00 pm, the water becomes clearer and even more majestic. The area’s deep waters and boulders to dive from see tourists travel from miles around to bathe in its virtually clear waters. And if swimming is not your thing, the area can be viewed from dry land on the metres of ricekerty woodern viewing bridges that surround the water’s edge.    Source |
Brazil's Carnival Gets Underway Despite Zika Fears Rio's five-day festival of dancing, bared flesh and wild costumes got underway in the face of warnings the Zika virus might make even kissing dangerous. Mayor Eduardo Paes handed a big golden key to the carnival's ceremonial King Momo, who promised a spectacular show. 'With great happiness, brotherly love and peace, I declare the best carnival on Earth open - our carnival in the marvelous city,' the dancing king, who is elected ahead of the festivities, said on Friday. The annual mega-bash famed for lavish and skimpily dressed samba parades and all-night street dancing is expected to attract as many as five million people.  In Sao Paulo, carnival celebrations were kicked off under intermittent summer rain, with a tribute to Carlinhos de Jesus, one of Brazil's most famous salon dancers   Revelers of the Perola Negra and Aguia de Ouro samba schools perform during the first night of carnival parade at the Anhembi Sambadrome in Sao Paulo Carnival Parade at the Anhembi Sambadrome  Regal delight: The floats kept on coming at the carnival which went ahead despite the current Zika virus scare which is gripping Brazil  Revellers of the Aguia de Ouro samba school perform during the first night of the carnival parade at the Sambadrome in Sao Paulo, Brazil   Smart outfits: A dancer from the Rosas de Ouro samba school performs (left) while a member of the samba school, Nene de Vila Matilde, (right) has fun on the streets  Glorious in blue: Performers dazzled on the streets as the annual carnival, which attracts five million people each year, got underway Source |
Drug-Resistant Bacteria Trumped with…Clay From Canada  Antibiotic resistant bacteria pose a serious threat to public health, often infecting vulnerable populations like hospital patients. But researchers in British Columbia may have found a solution that was hiding just below their feet all along: clay. Mineral Canadian clay exhibits antibacterial activity against a group of pathogens that are highly resistant to antibiotics, according to new research from the University of British Columbia. The researchers tested the clay’s reaction to a group of bacteria collectively known as ESKAPE pathogens – Enterococcus faecium, Staphylococcus aureus, Klebsiella pneumoniae, Acinetobacter baumannii, Pseudomonas aeruginosa, and Enterobacter species – named for their ability to resist the effects of antibiotics. As of 2008, they were responsible for the majority of hospital infections in the US. [b]"Infections caused by ESKAPE bacteria are essentially untreatable and contribute to increasing mortality in hospitals,"[\b] says Julian Davies, co-author of the study and microbiologist at the University of British Columbia. The researchers incubated various strains of pathogens with clay samples or only with water as a control and found that 16 strains of the bacteria samples died when incubated with clay. The clay, known as Kisomeet, came from a deposit northwest of Vancouver, and has been used by aboriginal Canadians for several centuries to treat ulcerative colitis, stomach ulcers, arthritis, and skin irritations, according to anecdotal reports. Source |
Source credit: Myron Levin Scientific research ties talc powder to ovarian cancer. Now Johnson & Johnson is facing a slew of lawsuits  Deane Berg’s doctor called her in the day after Christmas, 2006, to give her the crushing news. She’d had her ovaries removed, the pathology results were back, and they could not have been much worse. Berg had stage III ovarian cancer, and her prognosis was poor. Despite her 25 years as a physician’s assistant, Berg, then 49, knew next to nothing about ovarian cancer. Grappling with the “why me?” question, she studied the risk factors, finding just one that could apply: regular use of talcum powder for feminine hygiene. Talc powder might be a cause ovarian cancer–who knew? It turned out that some people did. Berg was stunned to learn that since the early 1980s, a slew of studies had found that women who regularly used talc powder for feminine hygiene had higher than average rates of ovarian cancer. Yet the evidence–which fell short of proving causation–was mostly confined to medical journals and had barely made a blip on the public radar. For millions of women, Berg included, dusting the genitals or underwear with powder was a daily ritual, like brushing teeth. Since her teens, Berg had used Johnson’s Baby Powder and Shower to Shower, another Johnson & Johnson powder marketed to women. “A sprinkle a day keeps odor away,” the ads said. “Your body perspires in more places than just under your arms.” How could a product meant for babies be dangerous? “This is crazy,” Berg recalled thinking. “Why aren’t they warning women about it?” So after painful rounds of chemotherapy, Berg filed a first-of-its-kind lawsuit against J&J in federal court in her home town of Sioux Falls, S.D. A mystifying verdict in October, 2013, enabled both sides to declare victory. The jury found Johnson & Johnson Consumer Cos., guilty of negligence for failing to warn of the risk of ovarian cancer, but awarded zero damages to Berg. More on this later. Yet the case brought a slow-building controversy to a head. Plaintiff lawyers, heartened by a liability finding in arch-conservative South Dakota, have since brought claims for about 700 ovarian cancer victims or their survivors, blaming the disease on exposure to talc powder. More cases are in the pipeline. Along with J&J, the suits name Imerys Talc America, Inc., part of the global mining concern that supplies talc to J&J. Other marketers of talc powder and the Personal Care Products Council, a Washington, D.C. trade group for cosmetics makers, are named in some of the cases. Lawsuits against Johnson & Johnson contend that women contracted ovarian cancer from using its talc powders for feminine hygiene. The company says there is no causal connection. “We use this on children … and it had to be a good thing, right?” said plaintiff Deborah Giannecchini, 62, a Modesto, Calif., hospital secretary diagnosed with metastatic ovarian cancer in November 2012. This is an ugly disease,” she told FairWarning. “I sure would have appreciated being given the chance to say this is worth the risk or it isn’t.” In J&J, “we’re dealing with a company that has done nothing to inform customers of the risk and, in fact, I believe has taken steps to hide the risk from the public,” said Ted Meadows, a lawyer with the Montgomery, Ala., firm of Beasley, Allen, which is involved in many of the cases. Imerys and the Personal Care Products Council wouldn’t comment, and J&J refused interview requests, but released a statement: “We have no higher responsibility than the health and safety of consumers who rely on our products. It is important for consumers to know that the safety of cosmetic talc is supported by decades of scientific evidence and independent peer-reviewed studies.” The companies contend that statistical associations between talc use and ovarian cancer are weak, and may result from bias in the study methods. A causal link is not biologically plausible, they say, since there is no proof that talc particles can pass through the genital tract to the ovaries or that, once there, they could cause malignant growths. There is no causal link, they argue, so warnings were unnecessary. Most of the lawsuits have been filed in New Jersey, where J&J is headquartered, or in state court in St. Louis, Mo., considered a favorable venue for plaintiffs. The first trials are scheduled for early 2016. About 20,000 U.S. women annually are diagnosed with ovarian cancer, and more than 14,000 die. Ovarian cancer strikes about one woman in 70. Studies showing a higher rate of the disease with talc use have typically found an increased risk of about 35 percent—which would put the odds at about one in 50. Talc, the softest of minerals, has a multitude of industrial and consumer product uses, including in the manufacture of paints, paper, rubber, roofing and ceramic materials, and even as a food additive, a filler in capsules and pills and in cosmetics. Complicating the health question is that talc deposits are often interlaced with other minerals, including asbestos. That means the danger, if any, may be due to impurities, rather than talc itself. Over the years, some groups of talc miners have been stricken with asbestos diseases. Talc suppliers have also paid settlements or judgments to factory workers, such as tire makers, who contracted asbestos-related illnesses following exposure to industrial grade talc. In 1976, researchers at Mount Sinai Hospital in New York published test results on 20 talc-based consumer products, including baby and facial powders. They found two types of asbestos, tremolite and anthophyllite, in 10 of the 20 products. That same year, the Personal Care Products Council (then called the Cosmetic, Toiletry and Fragrance Association) issued a standard requiring “a complete absence of detectable asbestos in cosmetic talc.” J&J vows that its talc is “asbestos free, as confirmed by regular testing conducted since the 1970s.” The ovarian cancer suits take the claim at face value, asserting that talc itself, not impurities, caused the disease. The suits charge J&J with failing to take the precaution of replacing talc with cornstarch, which has similar skin-soothing properties but has not been linked to health risks. While defending the safety of talc, J&J has offered powders with cornstarch or cornstarch-talc blends. In October 2012, for reasons neither company would discuss, J&J sold North American marketing rights to Shower to Shower to Valeant Pharmaceuticals. “Inaccurate, to phrase it euphemistically” Suspicions about talc and ovarian cancer go back decades. In 1971, British researchers analyzed 13 ovarian tumors under a microscope and found talc particles ‘’deeply embedded” in 10. In 1982, the journal Cancer published the first study showing a statistical link between genital talc use and ovarian cancer. Soon after, lead author Dr. Daniel Cramer, a gynecologist and Harvard Medical School professor, was visited by a senior scientist from J&J. He “spent his time trying to convince me that talc use was a harmless habit,” Cramer recalled in a document filed in court, “while I spent my time trying to persuade him … that women should be advised of this potential risk.” Altogether, about 20 epidemiological studies have found increased rates of ovarian cancer risk for women using talc for hygiene purposes, though some studies have found no association. One report, published by Cramer and several co-authors in 1999, said talc use could be the cause of about 10 percent of ovarian cancers in the U.S.–or some 2,000 cases per year. “Balanced against what are primarily aesthetic reasons for using talc in genital hygiene, the risk benefit decision is not complex,” the study said. “Appropriate warnings should be provided to women about the potential risks of regular use of talc in the genital area.” In response to such findings, the Cancer Prevention Coalition, an advocacy group, asked the Food and Drug Administration in 1994 to require warnings against talc use for genital hygiene. The agency said it lacked evidence to require warnings, and J&J refused to issue them voluntarily. Instead, the company and its allies circled the wagons. In 1992, the cosmetic and fragrance association launched a Talc Interested Party Task Force to develop talking points and find experts to rebut studies linking talc to ovarian cancer. But some statements by the trade group were “inaccurate, to phrase it euphemistically,” a consultant for J&J warned. In two 1997 letters to company officials (here and here), toxicologist Alfred P. Wehner attacked statements that “the scientific evidence did not demonstrate any real association between talc use in consumer products and ovarian tumors.” “There are at least 9 epidemiological studies published in the professional literature describing a statistically significant (albeit weak) association between hygienic talc use and ovarian cancer,” Wehner wrote. “Anybody who denies this risks that the talc industry will be perceived by the public like it perceives the cigarette industry: denying the obvious in the face of all evidence to the contrary. This would be a particularly tragic misperception in view of the fact that the industry does have powerful, valid arguments to support its position.” “Arrogance and insolence” As debate continued in scientific circles, the National Toxicology Program, part of the U.S. Department of Health and Human Services, ruled in 2005 that existing data were insufficient to list talc as a cancer-causing agent. The following year, however, the International Agency for Research on Cancer, part of the World Health Organization, classified talc as a 2B agent–“possibly carcinogenic to human beings,”–based on the “remarkably consistent” results of epidemiological studies. “A positive association was observed,” IARC said, “but chance, bias or confounding factors cannot be ruled out with reasonable confidence.” Industry officials have downplayed the significance of the IARC action, noting that coffee drinking is also listed 2B for possible links to bladder cancer. But emails produced in the Berg case show industry officials were deeply upset by the IARC ruling. A senior executive with J&J talc supplier Luzenac America (now known as Imerys), condemned the decision as “a travesty of scientific integrity.” Rich Zazenski, Luzenac’s director of environment and safety, declared in the Feb. 27, 2006 email to a J&J official: “I can’t believe the arrogance and insolence of this ‘U.N. agency.’” “Rest assured, we (I) will explore all possible avenues of challenge—not necessarily expecting a retraction—but to see what sort of political heat (with financial ramifications) that could and should be brought down upon IARC and WHO,” the email said. Zazenski died in 2008, and it’s uncertain if there was an effort to carry out the threat. In 2013, the industry cheered the findings of an expert panel of the Cosmetic Ingredient Review, a group that is funded by cosmetics manufacturers but says its reviews are independent. The panel declared that talc “is safe in the present practices of use and concentration.” A coveted image J&J was founded in the 1880s by the brothers Robert Wood, James Wood and Edward Mead Johnson. First aid kits, dental floss, sanitary napkins and baby powder were among their first products. Today, J&J is a $74 billion-a-year colossus with a workforce of nearly 129,000, more than 275 operating companies in over 60 countries, and a huge footprint in pharmaceuticals and medical devices, along with consumer health aids. Yet the Johnson & Johnson name still evokes cherubic infants and adoring moms, burnishing an image that most big companies can only envy. Fortune Magazine’s 2015 list of most admired companies ranks J&J first in the pharmaceutical industry and 11th of 668 companies worldwide. In December, the website CareerBliss.com, ranked J&J number one on its list of the 50 Happiest Companies in America, which honors businesses with the most contented workers. J&J last year won kudos for vowing to share clinical trial data with researchers, and for announcing it was testing an Ebola vaccine. In December, a 3 1/2 minute infomercial with singer-actor Jennifer Hudson on ABC’s “The View” touted one of J&J’s charitable endeavors. “What a great company they are!” enthused Rosie O’Donnell, then co-host of The View. “They’re a wonderful company that America’s believed in for so long.” Legal battles that have engulfed the company leave a different impression, however. Last month, J&J’s McNeil Consumer Health Care division pleaded guilty to a criminal charge of selling adulterated medicines, including children’s Tylenol and Motrin that were contaminated with bits of metal. The plea deal with the Justice Department, which included a criminal fine and forfeitures of $25 million, capped a series of recalls and enforcement actions stemming from quality control breakdowns at McNeil’s Fort Washington, Pa., plant. In November 2013, J&J and two subsidiaries, Janssen Pharmaceuticals and Scios, Inc., agreed to pay more than $2.2 billion to the U.S. and 45 states to settle criminal and civil charges of illegally promoting Risperdal and other anti-psychotic drugs for unapproved uses. They had also been accused of paying kickbacks to doctors and a major pharmacy to prescribe the drugs. As part of the settlement, Janssen pleaded guilty to a criminal misdemeanor. J&J settled the remaining civil allegations without admitting wrongdoing. The same month, J&J’s DePuy Orthopaedics unit announced an agreement to pay about $2.5 billion to compensate 8,000 patients who had surgery to replace allegedly defective DePuy hip joints. Earlier this year, the company reached a similar settlement with another 1,400 patients–yet it still faces thousands of injury claims related to the DePuy implants. By J&J’s count, at the end of 2014 it faced 56,300 personal injury claims in the U.S. involving three product lines: hip implants, Risperdal and pelvic mesh devices made by its Ethicon Inc. subsidiary. The talc litigation, on the other hand, wasn’t even get mentioned in J&J’s 2014 annual report. Still, the challenge has not been taken lightly. J&J has retained as lead counsel the firm of Shook, Hardy and Bacon, a go-to corporate defender that has represented tobacco companies, drug and auto makers in high-stakes litigation. In this together Deane Berg recalls her sense of shock and dread when she heard her diagnosis. Both she and her husband Jim broke down and wept. She got chemotherapy through a port in her chest. It was painful, nauseating—”to put it point blank, holy hell … It put my family through a lot, too,” Berg said. Her first husband had died of lung cancer from smoking, and her two daughters now feared they would lose their mom, too. One called Berg from college every day to make sure she was all right. “Once you get a cancer diagnosis … it never goes away,” Berg said. “There’s always that ultimate fear that it’s going to come back.” So far it hasn’t. Berg eventually returned to work as a physician’s assistant at the VA hospital in Sioux Falls. She figures her ordeal has made her better at the job. “It has definitely taught me how important it is to take time with cancer patients, to give them concern and caring, and to say ‘I know what you’re going through,” she said in an interview. “I give them a hug and say we’re in this together.” In studying the risk factors that might have led to her cancer, Berg mostly came up empty. Family history of ovarian cancer? No. Previous cancers? No. Mutations in the BRCA 1 or BRCA 2 genes? No. Use of fertility drugs; never having been pregnant; eating a high-fat diet—no, no and no. But some literature cited another possibility–genital use of talc. Berg posted a question on the website of the National Ovarian Cancer Coalition, asking if anyone had used talc and contracted ovarian cancer. Soon she was contacted by a Mississippi lawyer named Allen Smith. After checking him out “to make sure he was legit,” Berg said, she authorized Smith to order an analysis of her tumor tissue. Talc particles were found inside. Explaining her decision to file a lawsuit, Berg told FairWarning: “I don’t want other women to suffer like I did if this could be prevented.” Her case was tried in fall 2013. Medical experts for J&J dismissed the idea that talc caused her cancer as biologically implausible. They explained the discovery of talc particles in the tumor tissue as probably due to contamination, a common problem in hospitals. Berg’s lawyers sought to discredit the defense experts as hired guns, noting that two had testified on behalf of tobacco companies. In its head-scratching verdict, the jury found the J&J subsidiary, Johnson & Johnson Consumer Cos., Inc., guilty of negligence for failing to warn Berg of the ovarian cancer risk. Though she had suffered losses—months of lost work time, permanent hearing loss and numbness in her hands and feet from chemotherapy; and the endless fear of her cancer coming back–the jury awarded no damages. Berg said her lawyers were “dumbfounded,” and that she attributed the result to South Dakota being “a very conservative state.” It tempers her anger to consider the big picture. “I’m lucky to be alive—really, really lucky,” she said. “I count my lucky stars, let’s put it that way, that I’m not gone.” Contacted by FairWarning, jury foreperson Christina Wilcox explained the compromise verdict. Jurors decided that “the actual medical proof [that talc caused Berg’s cancer] was not there,” she said. “She [Berg] just got handed a bad deal.” “However, we also felt that Johnson and Johnson should consider putting…something on the product to alert the consumers of the possible injury and the possible risk,” Wilcox said. “Let the consumer decide what they want to do.” |
Credit to King A-Maz for the heads-up Last month, a story ran about a rich dad from Atlanta buying a Nigerian as a toy for his 13 year old son, and our Nigerian blogs ran with it. However the story is a hoax and was reported by Stuppid.com, a website notorious for its hoaxes and satirical news stories. They even went as far to post a supposed picture of the kid and the ‘toy’. The truth is Stuppid.com is just a satirical site. They make up stories they deem funny and publish. They are not an actual news reporting publication. Other stories on the site are just as ridiculous, e.g Alabama Church Converting Insects To Christianity; Texas Woman Pregnant With Satan’s Baby; and so on. Original Stupid story here |
Zaheer Ahmed compiled a list of freely available and downloadable Programming languages books. The list contains almost all the programming languages and technologies. The books are free as in FREE while a few might require email registration. Most are downloadable pdf's while others are web books. Download, learn and share. Page link here 1 Like |
Source/Credit: Wired Company Pays Nigerians to Learn Computer Programming  Yetunde Sanni, Nadayar Enegesi (standing), Kosi Anyanwu, and other participants of Andela’s female-only Boot Camp. Mohini Ufeli Chibuzor Obiora was an out-of-work TV news anchor in Lagos, Nigera when he came across a curious link on Twitter: a company was offering money to people willing to take a course in computer programming. For Obiora, it sounded too good to be true. “I was always interested in learning [to code] because of the problem solving aspect of it,” he says, “and here was a firm that promised to pay you to learn.” But it turned out to be a very real opportunity. The company is called Andela. It’s based in New York City, and it pays Nigerians to learn programming skills before putting them to work on projects that serve businesses back in the States. After about four months of training, Obiora now works under Andela as a web development contractor for an (unnamed) U.S. based organization—all without leaving Nigeria. The ultimate aim is to tap the vast pool of talent found in countries that aren’t exactly known as technology hubs, including not only Nigeria but other parts of Africa. “We know that brilliance is relatively evenly distributed across the human population,” says Andela co-founder Jeremy Johnson. “In terms of pure aptitude, there are genius level people across the world. But what there’s not is equal opportunity.” ‘We know that brilliance is relatively evenly distributed across the human population’ Today, U.S. tech companies aren’t shy about saying they have trouble finding programming talent. Critics argue this talent shortage has more to do with stinginess and selective hiring practices than a real lack of qualified programmers, but regardless of the reasons, the need is there. As a result, a new wave of services are working to train enormous numbers of new programmers. The operations range from online tutorial services like Codecademy to the dozens of “code bootcamps” that promise to get people job-ready in a matter of months. Andela puts a new twist on the bootcamp idea by moving them overseas—and paying people to participate. The Test Johnson, who previously founded the online education company 2U, launched Andela earlier this year, alongside Christina Sass, who has a background in non-government organizations, Iyinoluwa Aboyeji, a Nigerian entrepreneur who previously co-founded the online education companies Bookneto and Fora, and Ian Carnevale, who was also a co-founder of Fora.  Blessing Orazulume and other participants of Andela’s female-only Boot Camp. Mohini Ufeli To find good students, Andela gives people like Obiora an online aptitude test that gauges their reasoning and logic skills. Then it interviews the top 10 percent, accessing their “soft skills,” such as interpersonal communication. Those that pass this phase go on to a several-month training program, not unlike the code bootcamps in the U.S. But not many make it this far. “It’s the most selective training program on the African continent,” Johnson boasts, saying the company only accepts about 0.8 percent of applicants. Those who are accepted get access to educational resources that are scarce in Nigeria. One student, Tolulope Komolafe, says her computer science courses in university didn’t involve any actual programming. The teachers just wrote code on a chalk board. “During the first two weeks of training I discovered that I actually knew nothing about coding,” she says. The Guild Analogy Students who finish at least 1,000 hours of training are then eligible to work as web developers for Andela’s clients, but they continue to learn new skills. Johnson says most students will spend about two-thirds of their time working for clients, and the remaining time on education. All told, both the students and staff work about sixty hours a week. “It’s very similar to the way that guilds worked in the middle ages,” Johnson says. “You get paid a small amount as an apprentice, then you work as a journeyman with lots of other craftspeople, and eventually become a master.” Johnson says the company charges clients about half of what they would pay a domestic developer, and that students are payed a middle class income in their home countries throughout the program, including during the training period. But he declined to provide specifics. Obiora says that the compensation is fair and that it’s more than he made at his previous job as a news anchor at a local television station. A New Kind of Off-Shoring Offshoring development work is nothing new. But Andela does things a bit differently. Instead of its students handling a client’s project on their own, they work hand-and-hand with workers inside the client company. Obiora, for example, participates in his client’s Slack chat room, uses the same project management tools they do, and he’s part of the same email conversations that drive those projects. Like other Andela students, he works the same hours as his U.S. counterparts. As for the quality of the work, Andela’s developers are on par with local junior-level web developers, says Scott Gerber, founder of Young Entrepreneur Council, an invitation-only organization for entrepreneurs under 40 that hired Andela to help build new features for its web-based member services. “I was skeptical at first,” he says. “I thought: ‘Outsourcing development? I’ve seen this before, I know how it turns out.’ But I can’t speak highly enough of them.” He says that he prefers to hire locally, and that he does have many developers in the U.S. But ultimately, he can’t find enough coders. “It’s very difficult to get developers at the caliber we need at a price we can afford,” he says. “We’re a multimillion dollar organization, but we still can’t compete with Google or Facebook for hiring.” Update 3:15 PM EST 12/18/2014: This story has been updated to include mention of Andela’s fourth co-founder, Ian Carnevale. |
Link Here Developers of the World Let's Hack Together! Traditional hackathons are all about the location and although we love the good old fashioned way of hacking together an awesome project, our browsers are now strong enough that distance is of no consequence when it comes to creating awesome projects. We can and should get together to write code and create awesome projects, regardless of where we are. Welcome to the World’s First Global Virtual Hackathon! This event is intended to connect developers across the globe and get them to code together irrespective of their locations. You will problem solve and build with old or new team members and try to win! How does it work? First, sign up using the simple form above. We will send you a short questionnaire that will help us understand a little bit more about you and your team’s background. We promise to keep it short and sweet. Applications can come from individuals or teams of up to 5, however each team member needs to be a contributing team member (writing code or designing). If you are an individual who is selected and are looking for team members, post a message on the #hackathon channel on Koding. Your post should clearly articulate what type of skill set you are looking for and what type of skill set you have. e.g.: I am a nodeJS developer looking for a backend database team member. Once you get a response, jump into private chats on Koding itself to discuss your ideas and start recruiting! How do I get accepted? We expect a lot of you to apply but to keep things sane, we will be limiting the final competition to 1000 teams. Our panel of judges will decide who will be part of the competition. Their decision will be based on factors like location, team size, project work on github, social presence, etc. Applications are being reviewed on a first come first serve basis so apply today and if approved, you will receive an email from us with further instructions. We will also let you know if your application is not approved. What is the theme for the Hackathon? We will provide a few themes for the hackathon. Your task will be to use publicly available resources (APIs, data sets, graphics, etc.) and your imagination to create a project that addresses one of the the themes of the event. You can expect the themes to revolve around topics like: Global finance, Education, Healthcare, Climate change, Travel, etc. On Nov 21st, the hackathon themes will be announced on the #hackathon channel on Koding. We will also email the themes to all teams that are accepted into the event. What are the rules? Our goal is to ensure that all teams have a level playing field; therefore it is imperative that all code, design, assets, etc… must be created during the duration of the event. No exceptions. You can brainstorm ideas prior to the event, however any assets or code used as part of your submission must have been created during the event. The only exception to this rule is the usage of publicly available material. This includes: public code snippets, images, open source libraries and projects, public APIs, etc. You get the picture. We will request a review of all the code you submit as part of your hackathon project to ensure that it has been created during the hackathon period (Dec 6th - Dec 7th). Being engineers ourselves we are savvy to what can and can't be created in 48 hours.  Play fair! What are the prizes? $10,000 cash prize from Koding, split amongst the top 3 teams ($5k, $3k, $2k each). Winners will be offered credits for services like DigitalOcean, Tutum and many more! Winners will be offered interviews with investors on our judging panel. Who will eventually own the projects created? You will retain full ownership and rights to your creation. Be super awesome and have fun! Get creative, meet new people, make new friends and problem solve with them. What is the schedule? Now - Registration open. Nov 21st, 1200 PDT - Applications are closed. Final notifications are sent to teams/individuals who were accepted and the Hackathon Theme is announced (on the #hackathon channel on Koding and via email to the accepted teams). Dec 6th - Day 1 Let the hacking begin! Dec 7th - Day 2 of the Hackathon 0000 – 2200 PDT Hacking continues 2330 – 2359 PDT Teams submit their projects to hackathon@koding.com (see section below on how to submit) Dec 10th - Winners are notified via email and winning projects are listed for public viewing. What is the judging process? Due to the large number of teams and potential hosting pitfalls that can come with, we request that each team submit their project using a Koding VM. Don’t worry, you don’t need a paid account. If you submit your project and your VM is turned off due to inactivity, we will turn it on for you. Judging will happen in three rounds: Round 1: All projects submitted for this round are distributed (ad-hoc) to our judges panel and they will evaluate it based on API’s used, complexity of solution, adherence to the theme, team size, geolocation of team, etc. Selected projects move to round 2. Round 2: Teams reaching this stage will have their projects evaluated on stricter versions of the same criteria above and will be exposed to our entire judging staff. Each judge gets to assign points (1-10) and the top 10 teams scoring the most move to the final round. Round 3: Judges meet (virtually of course) for a live call to discuss and pick the final 3. How to submit your project Send the following details to hackathon@koding.com Koding VM URL where the judges can see your project. A brief description of your project (not more than 250 words). A brief introduction to your team members (who did what). How your project addresses the theme of the hackathon. What tools did you use to collaborate. Your submission should have a time label less than Dec 7th 2359 PDT. Submissions received after the deadline will not be considered. No exceptions. |
@CyberG --> The first practical solution to the issue i have come across on Nairaland. @Seun ---> The rabid tribalism, ignorance and crass stupidity exhibited by some members are a big turn off and limits my visits and interactions to the barest minimum in recent times . Excuse me if i'm mistaken, seems i did mention (some time ago) something to the effect that you could take a look at Reddit and implement some of the good things in use there. Reddit implements an algorithm some what similar to what @CyberG noted above. However, even the Reddit ranking system is not perfect (i know 'cause i'm active there) but you could work out your own implementation with a little effort. 2 Likes |
Link Here.
1 Like |
Source Here An Explanation of the Evidence of Weaknesses in the Iron Dome Defense System Editor’s Note: Readerly response to a recent news story, “Israeli Rocket Defense System Failing at a Crucial Task, Expert Analysts Say,” where Ted Postol was quoted to say that Iron Dome was not effectively detonating warheads, was so negative, and angered so many people, particularly Israelis, that we asked Professor Postol to explain how he came to his conclusions and to show his data. He gracefully agreed. The following article represents his opinion, and is not necessarily the opinion of MIT Technology Review—and does not represent any collective assessment by MIT or one of its departments, labs, or centers. (That’s because we are editorially independent of the Institute.) Introduction In the early weeks of July 2014 the conflict between Israel and Palestinians in Gaza has again flared up. This has resulted in a new round of large-scale rocket attacks launched by Hamas, operating from Gaza, against Israeli population centers. The last time such large-scale rocket attacks occurred between Hamas and Israel was in November 2012. During the November 2012 conflict a large number of photographs of Iron Dome interceptor contrails were observed in the sky. These contrails revealed that the Iron Dome interceptor rate was very low—perhaps as low as 5 percent or below. This paper explains why the geometry of the contrails photographed in the sky indicates whether or not an Iron Dome intercept attempt had any chance of intercepting an artillery rocket target. I will show sample pieces of data indicating that Iron Dome performance was very low in November 2012, and I will show similar data for July 2014, which indicates that Iron Dome performance almost a year and a half later has probably not improved. At this time, collection of the data for July 2014 is still in progress. However, all the data I have so far collected indicates that the performance of Iron Dome has not improved. One of the most demanding problems in intercepting an artillery rocket is that the interceptor must destroy the warhead on the rocket. If the interceptor hits the back end of the rocket, all that will happen is damage to the expended rocket motor tube, which is basically an empty pipe. Damaging the back end of the artillery rocket essentially has no effect on the outcome of the engagement. The pieces of the rocket will essentially fall in the same defendant area, and the warhead will almost certainly go on to the ground and explode. These facts mean that the only meaningful definition of a successful intercept is the destruction of the artillery rocket warhead. As will be shown in the discussion to follow, destroying the artillery rocket warhead is considerably more demanding than doing damage to other parts of the artillery rocket—or successfully damaging an aircraft, causing the failure of its mission. Protecting a population spread over defended areas from the hazards of such missile attacks must involve protection against falling debris, which can cause serious injuries to individuals who are not in protective shelters. As I will discuss later in this article, Israel does in fact have an extremely effective missile defense. That defense is the early warning system that tells people on the ground a rocket is traveling in their direction, and the shelters that are arranged so that individuals can easily get to protection within tens of seconds of warning. In an article referenced later in this paper, it is shown that during the bombing of London by V-1 and V-2 rockets, seconds of early warning vastly reduced casualties and deaths from individual attacks. In the particular case of rocket attacks against Israel, the overwhelming number of artillery rocket warheads are in the 10- to 20-pound range, which makes the effectiveness of shelters even greater. These two factors, the small size of the warheads, and the warning and sheltering system completely explain why there have been no casualties from the rocket attacks. Assessing Whether or Not an Iron Dome Intercept Attempt Is Successful from Photographs of Iron Dome Contrails I will first show why the Iron Dome interceptor must approach the target artillery rocket from a frontal direction. I will then show that the Iron Dome interceptor has, for all practical purposes, no chance of destroying the warhead on incoming artillery rockets if the interceptor engages the rocket from the side or from the back. I will then present photographic evidence of contrails in the sky, indicating that Iron Dome interceptors were mostly chasing or engaging artillery rockets in side-on geometries. I do not know why the Iron Domes were not engaging most artillery rockets using the proper front-on geometry. However, it is clear that the Iron Dome radar tracking and guidance system is not working, as it is initially sending Iron Dome interceptors to intercept points that then result in the interceptor not being able to achieve the right geometry for a successful engagement against the artillery rockets. I will show photographs of contrails from November 2012 and from July 2014 indicating that the Iron Domes are still behaving erratically—resulting in continued very low intercept rates. Assessing the Meaning of Iron Dome Contrails To understand why the Iron Dome interceptor must approach the artillery rocket from a frontal direction, it is necessary to have a rudimentary understanding of the Iron Dome interceptor. Figure 1 below shows a conceptual picture of a front-on engagement by an Iron Dome interceptor against a Grad artillery rocket. The blue dashed line emanating from the forward section of the Iron Dome interceptor depicts the line of sight of what is called a “laser fuse.” The purpose of the laser fuse is to create a beam of light that will reflect off the front end of the artillery rocket so that the interceptor can determine that the target artillery rocket is in the process of passing the interceptor. As can be seen from the diagram, the warhead in the Iron Dome interceptor is placed well behind the fuse assembly, a distance of roughly three feet from the laser-fuse aperture. This gives the fuse enough time to determine where the front of the target rocket is, estimate how long it will take for the front of the artillery rocket to pass parallel to the artillery rocket’s warhead, and detonate the Iron Dome warhead. The timing delay is quite critical to many variables. It must account not only for the location of the target rocket’s warhead but also for the speed of the fragments from the Iron Dome warhead, the miss distance, the off-parallel orientation of the Iron Dome interceptor relative to the artillery rocket, and the high passing speed of the Iron Dome interceptor and the artillery rocket. Figure 2 shows how the fragments move, under the assumption that the crossing speed of the Iron Dome interceptor and artillery rocket is about 1,200 meters per second and the fragments from the Iron Dome warhead are projected at about 2,100 meters per second perpendicular to the axis of the Iron Dome interceptor. Because the Iron Dome interceptor is moving at 1,200 meters per second relative to the artillery rocket, the additional crossing speed needs to be added to the 2,100-meter-per-second lateral velocity of the fragments. The net direction of the cloud of fragments, as would be seen if an observer were sitting on the artillery rocket, is shown by the pale blue arrow that passes through both the Iron Dome warhead and the artillery rocket’s warhead. Figure 3 shows the outcome if everything works as intended. However, there is a range of possible outcomes where success is very likely, and beyond that range, the possibility of success diminishes drastically. As can be seen from the arrow marked “1,500 meters per second” in figures 2 and 3, the higher crossing speed can result in a significant change in the net direction of the cloud of fragments. Thus, the fuse must determine the best time to detonate the warhead based on the crossing speed, the distance of the artillery rocket target as it passes by the Iron Dome interceptor, and the various fusing delays associated with detonating the Iron Dome interceptor’s warhead. Because of the uncertainties in the exact crossing speed and crossing geometry, even a perfect fuse may fail to put lethal fragments onto the artillery rocket’s warhead. In addition, unless the distance between the Iron Dome warhead and the warhead of the artillery rocket is small (roughly a meter or so), there will be a greatly diminished chance that a fragment from the Iron Dome warhead will hit, penetrate, and cause the detonation of the artillery rocket warhead. Thus, a front-on engagement does not guarantee that the Iron Dome interceptor will destroy the warhead on the artillery rocket. Figure 4 and figure 4A show the consequences of a failure in the fuse timing in what was almost certainly an engagement between an Iron Dome interceptor and the artillery rocket shown on the ground in the photos. As can be seen by inspecting the photograph in figure 4, there is significant damage in the area where the rocket fell. This damage was almost certainly due to the detonation of the rocket’s small warhead. Figure 4A shows the magnified front end of the rocket, where holes can be seen in the expended and empty rocket motor casing that was immediately behind the warhead. This photograph therefore shows an example of what might have been a successful Iron Dome intercept attempt. In this case, it is nearly certain that the artillery rocket was engaged by an Iron Dome interceptor that was properly approaching the artillery rocket front-on. Unfortunately, the timing commands from the fuse resulted in fragments from the exploding Iron Dome warhead hitting the artillery rocket after the warhead had passed. The relatively low density of holes in the artillery rocket’s afterbody suggests that the encounter also had a relatively high miss distance—possibly several meters. This photograph illustrates how even when the Iron Dome interceptor is in a proper front-on trajectory, it can still fail to destroy the warhead of a target artillery rocket. Figures 5, 6, 7, and 8 show detailed vector diagrams that indicate how the Iron Dome interceptor would perform if it engaged an artillery rocket from a variety of directions. In these diagrams the speeds are shown in feet per second, rather than the meters per second used in figures 1, 2, and 3. Figure 5 shows a nearly front-on engagement direction (again, note that all the vector speeds are now in feet per second). A careful review of the geometry of the engagement will reveal that even a moderately skewed off-frontal direction of approach will drastically reduce the chances that fragments from the Iron Dome warhead could be sprayed onto the warhead of the artillery rocket. This therefore shows that the front-on geometry is very sensitive to small off-frontal errors that could be the result of faults by the master control system in the guidance and control of the Iron Dome interceptor. This particular diagram (figure 5) demonstrates how important it is for the the master guidance and control system to place the interceptor in the right location before it begins the actual homing process against a target artillery rocket Figures 6, 7, and 8 show detailed vector diagrams for interceptor engagements that approach the target artillery rocket from the side or from the back. A careful inspection of the geometry of the fuse-sensing beam and the spray pattern of the fragments from the Iron Dome warhead show that there are two very serious problems with these kinds of engagements. First of all, if the fuse detects the artillery rocket, it has no way of determining where the warhead is on the artillery rocket. Second, it is nearly certain that even if the fuse detonates by chance at a time when the warhead might be in the spray pattern of the Iron Dome warhead, the distance between the Iron Dome warhead and the artillery rocket warhead will in almost all circumstances be very large, resulting in a very low density of fragments at the location of the artillery rocket warhead. Given the small number of fragments that can be dispersed by the Iron Dome warhead, this translates into a very high chance that no fragment will hit the warhead. Making matters even more difficult, the projected area of the warhead is very small, since it will be encountered from the front or back rather than from the side. Moreover, fragments are very likely to hit metal surfaces that are at very low grazing angles relative to the direction of the fragment motion. This will result in fragments’ tending to bounce off the shell or transmit almost no energy to a target. Hence, figures 6, 7, and 8 show that for all practical purposes, the probability that the Iron Dome interceptor can destroy the warhead of the engaged artillery rocket is essentially zero. What does the data show about Iron Dome’s performance in November 2012 and July 2014? Figures 9, 10, and 11 show contrails in the sky that indicate that Iron Dome interceptors were attempting to engage target artillery rockets either by chasing them from behind or by attacking them from the side. The geometries of the engagement are easily established because the artillery rockets are falling at high elevation angles relative to the ground—perhaps 60 to 70 degrees relative to vertical. This reëntry angle is due to aerodynamic drag, which slows up the artillery rocket and eventually causes it to fall at a relatively steep angle. Figures 12 and 13 show photographs that are supposed to have been taken in July 2014. I have found photographs from November 2012 that have been mislabeled as being from July 2012, so I am in the process of verifying that photographs collected were actually taken in the stated time frames. These two photographs have checked out as being from July 2014. Figure 14 shows a very rough estimate based on my observations in November 2012, when I saw perhaps no more than 10 to 20 percent of Iron Dome contrails that indicated an engagement geometry that was front-on. As shown in the performance “guesstimate,” if we assume that the engagement geometry and 20 percent of the engagements were front-on, then at that time I estimated the probability of destroying a SCUD warhead might be between 0.3 and 0.6. Thus, if all other engagements effectively resulted in a zero probability of intercept, then the intercept rate would be roughly 0.2 × (0.3 or 0.6) = 0.06 to 0.12 That is an intercept rate, defined as destruction of the artillery-rocket warhead, of between 6 and 12 percent. My best estimate is that fewer than 20 percent of the engagements I was able to get data on were actually front-on, and I have no information about the actual miss distances or whether the engagement-attempt geometries were close to antiparallel. Thus the statement that the intercept performance of Iron Dome appears to be probably 5 percent or less. A sample of such a calculation is shown in figure 14. Why Are Israeli Casualties from Rocket Attacks so Low? An article published in the journal Nature in 1993 addressed the debate over the performance of the Patriot missile defense in the Gulf War of 1991. At that time, the same questions were being raised—why was damage so low, and why were there so few casualties? (All reports now indicate that there was only one casualty from the direct effects of the SCUD attacks. This casualty was caused by a Patriot missile that dove to the ground in an attempt to intercept a SCUD missile.) In the case of the SCUD attacks, there were many fewer rockets launched at Israel (perhaps around 40), but the warheads on the missiles were much larger—about 500 pounds. Nevertheless, many SCUD warheads fell in open areas, doing relatively little damage. In cases where warheads fell near buildings, the civil-defense measures essentially protected the population from the consequences of the SCUD impact. Figures 15, 16, and 17 show damage in Israel from artillery rocket attacks during November 2012 and July 2014. As can be seen by inspecting the photographs, even when the rockets happen to hit buildings, the damage tends to be quite localized. This does not mean that individuals in the area of the rocket attack would not be injured or killed if they were close enough to the impact site, but it is very clear that the warheads are not of sufficient size to cause casualties or deaths to those who are properly sheltered. In contrast, figures 17 and 18 show the results of bomb attacks in Gaza in July 2014. The exact yields of the bombs are uncertain, but it appears they are probably in the 1,000- to 2,000-pound category. In these cases, attempts at sheltering the population might well fail, as few shelters can sustain the level of damage that could be inflicted by such large bombs. So again, this illustrates that the small size of the artillery rocket warheads and the ability to quickly warn populations of these arriving small warheads is an extremely capable defense that works far more effectively than Iron Dome. Theodore Postol is Professor of Science, Technology and National Security Policy in the Program in Science, Technology, and Society at MIT.  Figure1  Figure2  Figure3  Figure4  Figure4A  Figure5  Figure6  Figure7  Figure8 |
Scientists discover the first real reason we need sleep:  The image above, from Xie et. al in Science, shows how when mice sleep, fluid-filled channels (pale blue) between neurons expand and flush out waste. We know we need to sleep. We know our brains and bodies work better after sleep. But what we didn’t know, until now, was why. Scientists have just reported the first major mechanical reason our brains need to sleep — certain cleaning mechanisms in the brain work better when we shut the brain down. Just like how dump trucks take to the city streets during the pre-dawn hours because there’s less traffic, our brain’s cleaners also work best when there’s less going on. “This study shows that the brain has different functional states when asleep and when awake,” study researcher Maiken Nedergaard, of the University of Rochester said. “In fact, the restorative nature of sleep appears to be the result of the active clearance of the by-products of neural activity that accumulate during wakefulness.” We’ve known that our brains consolidate memories during sleep and perform other important functions. There are also benefits to the body during sleep — resting allows our muscles, bones, and organs to repair themselves. It also keeps our immune system healthy. We know that sleep has all of these benefits, but until now we didn’t know any of the specific changes that bring about these sleep benefits. Charles Czeisler, a sleep researcher at Harvard Medical School in Boston, told Science Magazine’s Emily Underwood that this is the “first direct experimental evidence at the molecular level” for why we need to sleep. The paper was published in the journal Science on Oct. 17. Toxic cells All of our cells accumulate waste while they are working, and these waste products can be toxic. If they aren’t removed they can build up and kill our cells. Throughout the rest of the body the lymphatic system washes these waste products away, but the brain is cut off from these actions because of the blood-brain barrier. When the brain is sleeping, channels between cells grow. This allows cerebrospinal fluid into the depths of the brain tissues to flush out toxic proteins that build up during the day, including the kind that are responsible for neurodegenerative diseases like Alzheimer's. The image above, from Xie et. al in Science, shows how when mice sleep, fluid-filled channels (pale blue) between neurons expand and flush out waste. Credit Here. |
 These images of Miley Cyrus above do not depict the act of twerking. Unfortunately, though, she is up for TIME's "Person of the Year" award, supposedly for her "twerk-filled performance at the 2013 MTV Video Music Awards," which "set off a chain of memorable entertainment moments." But here's the thing: She's never actually twerked at all. And even if she had, there is a slim chance she understands the African roots of the dance that she's come to so shamelessly own. Twerking is a complex and challenging dance move that originated in West Africa in the 1990s. It does not involve simply bending over and shifting your booty from left to right. As Christiana Mbakwe wrote, "It takes tremendous skill and attention." Shannon Givens, 25, said that it's extremely difficult to master. "Cold fact. Miley Cyrus is not twerking. She is moving side to side." Real twerking looks something like this: [flash=400,400] https://www.youtube.com/watch?v=xjOiJ4U4pNY[/flash] It seems like a new trend, but it's been around for awhile. In the book Playing with Identities in Contemporary Music In Africa, author Simon Akindes writes that twerking has its roots in West Africa. In the Ivory Coast, it's known as mapouka, and and they've been dancing it since 1997 (at the latest), when it hit the dance and music scene. The government temporarily baned the dance from all media, deeming it too provactive. The ban was lifted in 1999 when a new government took power. The New York Times wrote back in 2000, "Banned from Ivoirian television — chased away by officials in neighboring countries like Togo, Niger, Burkina Faso and Benin — mapouka spread nevertheless along the West African coast, from Dakar to Kinshasa, in the last couple of years. The dance — which focuses on, though is not limited to, the surprisingly difficult act of wiggling one's buttocks without moving one's hips — also became an endless source of discussions and newspaper ruminations on culture, sex, women and men, especially here in the Ivory Coast." [flash=400,400] https://www.youtube.com/watch?v=_Zw7PCVGYr4[/flash] Givens, who lives in Harlem and is studying at Long Island University's school of public health, was born and raised in the Sumner, Mississippi. She said that twerking migrated from West Africa into Caribbean culture before making its way to the American South, where it mainly picked up in Atlanta and among the Louisiana Bounce music scene. Mbakwe wrote, "I’ve seen variants of twerking my entire life. I remember watching the elderly women dance at the predominantly West African church I attended growing up. If the right 'praise' song was sung, they’d grab a white handkerchief and dance their way to the front of the church. They’d rotate their hips and bounce their bums until they were barely above the ground." The dance is inextricably intertwined with music. In the book The Modernity Bluff: Crime, Consumption, and Citizenship in Cote D'Ivoire, author Sasha Newell claims that mapouka has its own musical genre. In modern day American music, praisings of booty shaking are endless. The band Queen declared that "fat-bottomed girls make the world go 'round." Rapper Mos Def dedicated his song "Ms. Fat Booty" to a woman whose posterior he praised for being "so fat that you could see it from the front." Eminem, in "Ass Like That," described — quite viscerally — his physical reaction to a seeing nice round behind. And who could forget, "Girl, shake that laffy taffy?" Sir Mix-a-Lot does not even need to be quoted; we know what he likes, (and he cannot lie.) Women, too, are proud of their voluptuous behinds and understand their power. Beyonce coined the term "bootylicious," warning men that they weren’t ready for all her "jelly," and Fergie claimed that her "hump, [her] lovely lady lump" could get a man "love drunk." The cultural ties to music and dance are undeniable, but a deeper look at the move reveals that its popularity has scientific roots as well.  Biologist Alfred Kinsey argued that a man’s passion for a woman’s rear end comes from the fact that the female buttocks is the primary visual feature during sex for primates, our close ancestors, who do the deed "doggystyle." Dr. Lionel Tiger, anthropology professor at Rutgers University, said, "The posterior view implies a level of intimacy." On the the pelvic rotation of the twerk, he said, "Primates like to see objects move." He believes that twerking is a way for the woman to signal to a man that she is primed for sex. "It’s very literal. We’re animals." Another explanation is that voluptuous rear ends are a female-specific trait. They result from estrogen, which encourages the girl’s body, after puberty, to store fat in the hips and the butt, giving us girls all that "junk in the trunk" and "all that ass inside them jeans," to use Fergie’s poeticism. It’s a certain type of fat, though, containing adipose tissue, which stores energy for reproduction. Devendra Singh, a professor of psychology largely known for his work regarding the science of human attraction, wrote that — whereas a woman assesses a male’s desirability as a mate based on his control over resources — "physical attractiveness [for males] is largely a reflection of reliable cues to a woman’s reproductive success." So a curvy behind signals to a male that the female is able to get pregnant, carry to term, and successfully lactate in order to feed the baby, hence, helping the male’s offspring survive. (What would Darwin say about twerking?)  This might explain why the New York Times wrote that in the Ivory Coast, "As young women sought to outperform one another, a large posterior became de rigueur." The dance "made plumpness fashionable even among Westernized young women who had toyed with slimness." Twerking incorporates global cultures and histories, the freedom of sexual expression, and the evolutionary science of attraction. It transcends cultural boundaries and time periods. It's too bad that it's been reduced to a Miley Cyrus joke. Especially when she wasn't even twerking to begin with. Credits: Here. |
(1) (2) (3) (4) (5) (6) (7) (8) (of 8 pages)
(Go Up)
| Sections: politics (1) business autos (1) jobs (1) career education (1) romance computers phones travel sports fashion health religion celebs tv-movies music-radio literature webmasters programming techmarket Links: (1) (2) (3) (4) (5) (6) (7) (8) (9) (10) Nairaland - Copyright © 2005 - 2024 Oluwaseun Osewa. All rights reserved. See How To Advertise. 388 |